Cyber Attack Crisis (Part 2 of the Alien Deception Distraction)
by Dan Fournier, Opinion, published Thursday, Aug. 31, 13:12 EDT on fournier.substack.com
This is Part 2 of the Alien Deception Distraction.
Part 1 was all about exposing how the Alien Deception operation has been put in place to distract the masses from what is really coming.
I strongly suggest that you read Part 1 or at least have a serious look since it provides essential background information on why a crisis is needed at this particular juncture in time and how they are typically implemented. Knowing what has occurred in the past helps us look into the future.
Since this will be another relatively long post, feel free to skip directly to section 3 (The Next Crisis: A CYBER ATTACK), for what I anticipate will be the next big crisis that will be thrust upon the global masses, for the other sections mainly provide the underlying background and contextual information which support the likelihood of this presumptive attack.
This post, is structured as follows:
1. Introduction & Recapping Part 1
In Part 1, I posited that the recent flurry of news about UFOs/UAPs (Unidentified Aerial Phenomenon) and the revelation of so-called recovered extraterrestrial beings is merely serving as an elaborate distraction to keep the masses’ attention away from what they are really planning.
It was an extensive piece since a lot of background information needed to be covered, much of which focused on the fact that we are coming to an end of the current monetary/financial system which has been in place for more than a century.
This new global financial and monetary system will be a completely digital one (without cash) whereby every single financial transaction will be tracked and traced, leaving no room for financial privacy and financial freedom.
Moreover, a global Central Bank Digital Currency, or CBDC will serve as this digital form of money.
But a CBDC could not work without each and every citizen on the planet adhering to a Digital ID.
A major crisis is, therefore, required to justify to the masses that the time and need for a Digital ID has come (because of the crisis that is presaged in this post).
Specific historical examples were given in Part 1, along with a detailed description of the principal apparatus behind the current International Banking Cabal that runs the show. Select members of this cabal are extremely powerful individuals who operate in secrecy from the shadows, employing their globalist foot soldiers to carry out their agendas which consists largely of the political ruling class, billionaire philanthropists, and other useful-idiot corporatist elites.
As history consistently dictates and forewarns us, a crisis is required to imminently bring about such dramatic and pivotal changes.
2. The United Nations’ Plans leading up to 2024
Before getting into what is likely to consist of the implementation phase of the various plans that are in the works by the globalists, we need to look at their overall blueprint.
These are complex plans with many moving parts that are continually adjusted and tweaked, depending on several factors such as members states’ acceptability. International gatherings such as the G20 is but one means by which they get member states to be on board with their proposed policies.
Several supranational entities are integral to this broader plan, as they are controlled by the same elite families behind the International Banking Cabal (as I eluded to in Part 1).
Supranational simply means that they are international organisations consisting of many member countries, usually characterised by the fact that their executive leadership consists of unelected individuals who yield substantial amounts of power.
Apart from the United Nations (UN), the World Economic Forum (WEF) is also key since the two are basically tied at the hip in all matters of globalism and the implementation of the UN 2030 Agenda.
Secretary-General António Guterres (right) meets with Professor Klaus Schwab, Founder and Executive Chairman of the World Economic Forum. Photo credit and copyright: United Nations Photo/Manuel Elías.
In fact, the Partnership Framework signed between the UN and WEF focus on the facilitation and acceleration of the dystopian globalist agenda.
This 2030 Agenda should not be viewed in isolation, for it is part of a broader plan by which the elites are trying to gain global control.
Though the SDGs (Sustainable Development Goals) are the “heart and soul” of the blueprint, the following image provides the reader with a better understanding on how an ensemble of various programs are interlinked and come into play:
Road to the Summit of the Future. Image source: The United Nations’ Common Agenda The Summit of the Future in 2024.
There are four other parts that are of particular interest to us which I will cover:
2030 Agenda
Our Common Agenda (2021)
Summit of the Future (2022-2024)
Pact for the Future (2024)
I have already extensively covered the 2030 Agenda, so we will focus on other three below.
Our Common Agenda
The ‘Our Common Agenda’ consists of many policy briefs. These are policy documents that list what is to be agreed upon and accomplished by member nations in order to implement what they want to do.
I have written about Policy Brief 5 in my post The United Nations (UN) seeks Digital IDs for all, among numerous other Power-Grabs in which I criticise the power-grabs that the UN seeks to obtain – particularly with regards to their Sustainable Development Goals, or SDGs.
These global goals are craftily and deceivingly disguised to appear noble, but are actually quite nefarious.
Without getting into them too much, I will focus on two (of the 17) goals in particular: #1 NO POVERTY and #10 REDUCED INEQUALITIES – for which you can read a summary of each in the images below:
As I mentioned in that post, goals 1 & 10 are tied at the hip. The the phrase “mobile money” is common to both and essentially means a CBDC, or Central Bank Digital Currency.
In short, we can clearly see that their intention is to link a Digital ID to one’s bank account thereupon which people could “access financial and other services” in a CBDC system.
No Digital ID, no access to the system.
As I have already mentioned a few times now, the Digital ID is the indispensable KEY to the whole dystopian centralised global system by which they want to control us. In other words, if you control how one can spend their money, you essentially control them.
Also under the ‘Our Common Agenda’ rubric, we find the very controversial Policy Brief 2 – Strengthening the International Response to Complex Global Shocks – An Emergency Platform from March of 2023.
Why is Policy Brief 2 important?
Well, it is because it is the one that provides us with the best illustration of how they intend to consolidate power in the event of a global crisis, or “emergency.”
Here are some highlights from the policy brief (click link to access the PDF):
Centralised Standing Authority / Set of Protocols, or “Emergency Platform” (in the event of a global emergency)
Response from “International Financial Institutions”
Extension of the “Emergency Platform” at the discretion of the Secretary-General
Let me explain each of these three.
First, the policy brief calls for the formation of both an “Emergency Platform” and a “Standing Authority” or set of “protocols” that would be followed in response to a global “shock” or crisis (not that dissimilar to the Covid-19 Pandemic, for instance).
Think of the “Emergency Platform” as a kind of global response center that would dictate the set of responses (protocols) that could be activated in the event of a global crisis.
So far, this is only a proposal. But if accepted by member states, they would have to cede their respective national authority to the centralised “Emergency Platform,” and follow their prescribed response measures. As a tangible reference point, during the Covid-19 Pandemic, most nations followed the measures recommended by the World Health Organization (WHO) – that is part of the United Nations.
One of the most important recommendations for member states made in the policy brief is the following [with emphasis added]:
“j) Decide that the Secretary-General will convene the Emergency Platform in response to a complex global shock in consultation with the President of the General Assembly, the President of the Security Council, if appropriate, the relevant national authorities and regional organizations and the relevant United Nations entities, specialized agencies, international financial institutions and other multilateral institutions that are mandated to respond in the event of sector-specific crises;”
I’ve bolded the important part. It basically says that the Emergency Platform (the command center) will convene certain entities to coordinate and decide upon a response to whatever global crisis is being evaluated. Such entities can include ones from the UN such as “specialized agencies” like the World Health Organization (WHO), and “international financial institutions.”
Here’s the most important point; so, pay attention!
The policy brief is not fully transparent, for they do not reveal which entities consist of the “international financial institutions.”
Nevertheless, it is quite clear what is meant by them, namely that it would be the big three: The Bank for International Settlements (BIS), the International Monetary Fund (IMF), and the World Bank [Group]. Recall that the BIS is the “central bank of central banks” and, as such, yields power and command over each country’s respective central bank.
In the event of a global cyberattack (the premise of this series), the global financial system could come to a halt, requiring “international cooperation” by which we could easily see a coordinated response by financial institutions to implement strict protocols whereby participants (businesses and individuals) would be required to have a Digital ID for proper verification and permission to transact (and surf the internet).
In other words, it would no longer be “safe” to not have a means by which to properly identify every single participant who has access to the financial network. They will justify this bold requirement by saying that it will make it easier to track the “bad actors” who are behind these kinds of “cyber attacks,” to prevent or deter future large-scale “attacks.”
This would not be that different that the strict AML (Anti-Money Laundering) and KYC (Know Your Customer) measures that banks have implemented in the years following the so-called 9-11 “terrorist attacks.”
Different crisis, same playbook.
The specifics on how exactly this would play out are outlined in the next section of this post.
Section k) of the Recommendations of Policy Brief also show how they would get member states to be on board with the centralised global “Emergency Platform” response [with emphasis added]:
“k) Decide that, in the event of a complex global shock, the Secretary-General is requested to convene an Emergency Platform with the objective of:
i) Providing high-level political leadership by convening relevant actors to respond to complex global shocks;
iii) Leading the multilateral system’s response to a complex global shock to ensure a coherent and coordinated response;
iv) Leading a multi-stakeholder forum that can bring together all relevant actors that can contribute to the response;
vi) Securing clear commitments from key actors to support directly and immediately the global response to a complex shock;
By “multi-stakeholder forum” they, once again, are not transparent on who these “relevant actors” would consist of. But this is the type of language that is always used by the WEF to refer to their private-sector participants, or cronies.
Some of these participants are directly involved in cyber security.
So, in other words, the experts, actors, that would be involved in recommending responses to a cyber (or other crisis) would likely consist of private-sector participant who contribute to the WEF.
For example, the Cyber Peace Institute is one such private-sector actor that has been actively involved in matters pertaining to global cyber security with the WEF.
Before elaborating a little bit about this institute, let me just add one more point about the UN’s Our Common Agenda’s Policy Brief 2. It should be noted that the “Emergency Platform” global response center could retain their powers for as long as they wish, as per the following recommendation:
“Agree that, once activated, an Emergency Platform should be convened for a finite period determined by the type of shock and that, at the end of that period, the Secretary-General may extend the Emergency Platform for such time as necessary.”
Specifically, the Secretary-General (of the United Nations) – who is just a figurehead taking orders from his elite masters – could, at his discretion, “extend” the emergency protocols for “such time” as he sees fit.
Imagine, if you will, that the leader of this supranational organisation could single-handedly decide whether a coordinated global response could be prolonged for months, if not years.
They could use almost any fabricated global “crisis” – such as the false climate change one – to lock us down and impose freedom-crushing restrictive measures, similar, if not worse, than what we experienced during Covid-19.
The potential for usurping countries’ respective constitutions’ and human rights provisions would amount to nothing less than a form of totalitarian tyranny.
In the Conclusion of Policy Brief 2, it reads [with emphasis added]:
“We are living in a period of great uncertainty, yet we know that the risks we face are growing and becoming more complex. Enhanced international cooperation is the only way we can adequately respond to these shocks, and the United Nations is the only organization with the reach and legitimacy to convene at the highest level and galvanize global action.
My proposal to agree to protocols to convene and operate an Emergency Platform is a concrete step towards that goal. I urge Member States to seize the opportunity at the Summit of the Future to come together and agree on ways to strengthen our response to complex global shocks.”
The brief concludes that their emergency platform is the “only way” to go and that the UN is the only entity with the “legitimacy” to convene nations in a global response to a global shock.
Really?
Even high-level former United Nations insiders have admitted that the UN is not to be trusted. I reported on this in a previous post (The UN, WHO, & WEF seek to Sexualize, Exploit, & Decriminalize Sex with School-Aged Children):
“It also references a Rumble video to a documentary called Secrets of the United Nations whereby Calin Georgescu, a former executive director of the United Nations Development Programme (UNDP) who worked at the UN for over 20 years and testified before the International Crimes Investigative Committee that the UN is a platform for criminal oligarchs to execute nefarious agendas.
Georgescu also stated that the oligarchs behind the UN are pedophiles.”
I also referenced the video in which Georgescu heeds the dire warning.
The Cyber Peace Institute
Though many private players would contribute to a coordinated emergency response (some of which will be covered in Section 4 below), it’s worth looking at at least one in particular, namely the Cyber Peace Institute.
Firstly, we must observe that they always choose benevolent sounding names for their organisations. In this case, who wouldn’t want cyber “peace” – whatever that means?
Another common characteristic with organisations spearheaded and controlled by the financial elite is that they frequently based their headquarters in Geneva, Switzerland, where they are in proximity with each other and can obtain special status which includes total immunity from prosecution. The Cyber Peace Institution is no exception, for they are based in Geneva just like the BIS and the WHO.
If you look at who initially and is currently funding this NGO (Non-Governmental Organisation), you will notice the likes of:
William & Flora Hewlett Foundation
Ford Foundation
Bill Gates’ Microsoft
Financial behemoth Mastercard
In 2019, William & Flora Hewlett Foundation, Mastercard, Bill Gates’ Microsoft and the Ford Foundation provided the seed funding necessary to get the NGO up and running.
It is no secret that Bill Gates has his tentacles everywhere through Microsoft, the Bill & Melinda Gates Foundation, the Gavi Vaccine Alliance (also based in Geneva) and many other foundations he controls. Gates is also the largest contributor to the WHO. He, therefore, commands a lot of power over these institutions which seem to push the same types of agendas, including that of population control.
The same can be said about both the William & Flora Hewlett Foundation and the Ford Foundation who also collectively contribute millions to population control-related endeavours.
These founders are part of the extremely powerful financially elite class I have been referring to in this series.
It should also be noted that the Mastercard Impact Fund is also partnering with the Ford Foundation and the Rockefeller Foundation.
Furthermore, in 2022, the Open Society Institute – a George Soros funded outfit also contributed financially to the Cyber Peace Institute.
Needless to say, these donations always come with strings attached.
In short, we must not forget how these elites exert their power and influence through the endeavours undertaken by these foundations. Many may appear noble on the surface, but when you dig deeper, you often find more nefarious intentions, as is the case with their depopulation efforts.
Furthermore, Stéphane Duguin who is the CEO of the Cyber Peace Institute is an agenda contributor to the WEF and its Fourth Industrial Revolution, and is directly involved with cyber security policy shaping.
The case of the Cyber Peace Institute can serve as an illustration, or template model by which these elite families exert their power and influence in near obscurity, operating in the shadows cloaked by their subtly veiled philanthropic foundations.
That is their principal modus operandi which they have employed for centuries.
Stéphane Duguin doesn’t hide his tendencies for a centralised approach to “Internet Governance,” for he praises Geneva as being the ideal locale for maintaining “cyber peace.”
Switzerland, after all, has been sold to us as a so-called “neutral” country even though it has served as a lair for these supranational organisation and has sheltered them from prosecution and proper oversight.
Lastly on Duguin, he was also instrumental in the Cyber Polygon 2020 international online exercise which I will expand upon in Section 4 of this post.
As per news published by the Cyber Peace Institute, from May 19-20, 2022, they collaborated with Canada and the Kingdom of the Netherlands to host a hybrid workshop on Advancing the Cyber Programme of Action (PoA) in, of course, you guessed it – Geneva, Switzerland.
The Cyber Programme of Action (PoA), or Cyber PoA for short, was a secretive workshop; for, it was held under Chatham House rule which means that whatever was discussed is to remain private and confidential and cannot be revealed by members who were present at the meeting.
The Cyber PoA (archived here) built upon the 2021 UN Open-Ended Working Group on ICTs and International Security (OEWG) which is essentially a framework for “responsible state behaviour in cyberspace, as anchored in the applicability of international law, agreed norms of responsible behaviour and confidence-building measures (CBMs).”
It is not clear what is meant by “responsible state behaviour in cyberspace,” but we can roughly guess they imply that countries should follow the “international based order” regarding matters of cybersecurity.
The article further states:
“Currently, 60 States[1] are co-sponsoring the establishment of a UN PoA as a permanent, inclusive, consensus-based and action-oriented international instrument to advance responsible behavior in the use of ICTs in the context of international security.”
It’s not entirely clear what ICT stands for, but other articles refer to “ICT Threats” which are apparently those related to cybersecurity.
Their April 26, 2023 article Protecting critical infrastructure through the implementation of cyber norms deals with the “cyber threat landscape” which is “rapidly evolving with a rise in the frequency, sophistication, and intensity of cyberattacks.” The opening paragraph of the article further emphasises:
“Malicious cyber incidents against critical infrastructure have an important human component. These attacks put the population at risk of harm and expose the vulnerability of services on which our society and economies depend.”
This passage precisely describes the type of “global shock” as was shown earlier in the UN Policy Brief 2.
While preparing for potential cyberattacks is not a bad thing in and of itself, the Cyber Peace Institute, in coordination with the UN, doesn’t appear adequately transparent. For instance, they fail to reveal the name of their “Group of Government Experts,” their Open-Ended Working Group (OEWG) statements from members nations all point to broken links, and for the documents that are accessible they fail to mention who wrote them. In short, the whole endeavour comes across as sloppy and just a manufactured facade. But that doesn’t mean that they are done with it, for they can still try to get member countries to agree to international norms and laws.
Put simply, the Cyber Peace Institute and its coordination with the United Nations and WEF appears to be just another obscure front by which they can carry out their dubious attempts at subverting countries’ autonomy with regards to cybersecurity issues.
I personally don’t see this particular effort working out, but it nonetheless serves as yet another illustration of how they sneakily attempt to yield power away from countries in the name of an “international based order.”
Shamefully, the Liberal government of Canada has acquiesced and been much too obliging to these kinds of efforts.
In a Joint declaration following the third EU-Canada Joint Ministerial Committee meeting statement from May 16, 2022, Global Affairs Canada affirmed that they would at least be on board with what the European Union block and the UN are proposing with regards to cybersecurity-related issues. To wit, their statement includes the following:
“13. ...On cybersecurity, the EU and Canada pledged to continue to advance the application of international law, norms of responsible state behavior, confidence building measures and capacity-building initiatives, including in the UN through the establishment of the UN Programme of Action to Advance Responsible State Behaviour in Cyberspace.”
The linked document about the UN’s “Programme of Action to Advance Responsible State Behaviour in Cyberspace” essentially strongly reaffirms the framework for “responsible state behaviour in cyberspace” (see also point 17 of the Joint Declaration).
In addition, it shows how Canada intends to counter so-called disinformation through various means, as well as control how information is disseminated via what they refer to as “communications technologies.”
Moreover, point 13 links to the UN Programme of Action to Advance Responsible State Behaviour in Cyberspace which clearly shows how the UN and their partners want to accomplish these two goals [with emphasis added]:
“Recognizing that the dissemination and use of information and communications technologies affect the interests of the entire global community and that broad international cooperation would lead to the most effective responses,”
And the following passages really show us how they intend to silence dissent through censorship and blocking so-called misinformation:
“Expressing concern that information technologies and means of telecommunication can potentially be used for purposes that are inconsistent with the objectives of maintaining international stability and security and may adversely affect the integrity of the infrastructure of States, to the detriment of their security in both civil and military fields,
Expressing concern also about malicious information and communications technology activities aimed at critical infrastructure and critical information infrastructure facilities supporting essential services to the public,”
Stressing the urgent need to assist States in their efforts to implement the framework for responsible State behaviour and tackle emerging threats in the information and communications technology environment, as the ever-evolving properties and characteristics of new and emerging technologies expand the attack surface, creating new vectors and vulnerabilities that can be exploited for malicious information and communications technology activity,”
As is quite typical in UN documents (like is demonstrably the case with their SDGs), the language or lingo they use is intentionally cryptic or ciphered so as to obfuscate what they really want to accomplish.
Accordingly, I will simplify it for you with the following UN Lingo Translator to help clarify what is meant in the passages above:
“dissemination and use of information and communications technologies:” means how people post information online using “communication technologies” such as Twitter (now, called X), TikTok, Instagram, Facebook, and so on.
“malicious information”: means information posted online that is counter to their mainstream media’s prevailing narratives. This information may be factual, but it goes against what the arbiters of truth have decided (e.g., the Covid-19 vaccines are “safe and effective”).
“critical information infrastructure facilities:” includes real information systems, but also the mainstream media apparatus.
We can clearly see that they wish to install measures to control what information is permissible online and how it will be subject to censorship should it be deemed a threat to whatever they label as “critical infrastructure”.
In other words, dissenters or truth tellers will be categorised as legitimate cyber threats and thus subject to censorship and other punitive measures.
If the reader thinks this is merely conjecture on the part of this author, I would point to a press release from the United Nations dated just a few days ago titled Building a digital army: UN peacekeepers fight deadly disinformation which is calling for UN “peacekeeping operations” to employ a “digital army” to combat so-called mis- and disinformation on social media networks across the globe.
As is reported in The Epoch Times (also via ZeroHedge), the United Nations yet again cries for even more centralised power to maintain their foothold on the global narratives they wish to push.
And what better than yet another policy brief to help tackle this pandemic of mis- and disinformation? Well, that is exactly what the UN’s Common Agenda Policy Brief 8 – Information Integrity on Digital Platforms shamefully attempts to accomplish.
I will spare the reader with all the sordid and diarrheal verbiage contained therein, but will rather just list some of its concluding remarks so as to showcase the general gist of this utter fallacy:
“Strengthening information integrity on digital platforms is an urgent priority for the international community...
From health and gender equality to peace, justice, education and climate action, measures that limit the impact of mis- and disinformation and hate speech will boost efforts to achieve a sustainable future and leave no one behind.
Even with action at the national level, these problems can only be fully addressed through stronger global cooperation.
The core ideas outlined in this policy brief demonstrate that the path towards stronger information integrity needs to be human rights-based, multi-stakeholder, and multi-dimensional.
They have been distilled into a number of principles to be considered for a United Nations Code of Conduct for Information Integrity on Digital Platforms that would provide a blueprint for bolstering information integrity while vigorously upholding human rights.
I look forward to collaborating with Member States and other stakeholders to turn these principles into tangible commitments.”
Are we starting to see a pattern folks?
I think the reader is now well-equipped to decipher the lingo bolded in the above citation.
Summit of the Future (2022-2024)
The UN’s web page for the Summit of the Future in 2024 describes the “opportunity” as follows [with some emphasis added]:
“Major global shocks in recent years – including the COVID-19 pandemic, the Ukraine war, and the triple planetary crisis, among others – have challenged our international institutions. Unity around our shared principles and common goals is both crucial and urgent.
The Summit of the Future (September 2024) is a once-in-a-generation opportunity to enhance cooperation on critical challenges and address gaps in global governance, reaffirm existing commitments including to the Sustainable Development Goals and the United Nations Charter, and move towards a reinvigorated multilateral system that is better positioned to positively impact people’s lives. Building on the SDG Summit in 2023, Member States will consider ways to lay the foundations for more effective global cooperation that can deal with today’s challenges as well as new threats in the future.”
Wow, now that was a mouthful!
From this description, we can observe the prevailing and repeated themes: global shocks, “more effective” global cooperation, and the commitments towards Agenda 2030 and its SDGs.
It’s just more of the same nonsense.
They want to amass increasing amounts of power through centralisation.
They want to make it appear as though every shock or crisis is a global one, thus requiring a global response.
Moreover, they seem to always fail to understand that member states have different cultures, peoples, constitutions, political systems, legal systems, rights charters for citizens, and so on. And that trying to create blanket, uniform, global norms just won’t work.
They’ve tried it in their global response efforts with the Covid-19 crisis which proved to be an utter failure.
Yet, they are ignorant, adamant, and bold enough to continue to try and employ a global Band Aid for their next pre-manufactured crisis.
Pact for the Future (2024)
The Pact for the Future (2024) is simply the ambition of the United Nations to get heads of state/government to agree on the various frameworks and blueprints set out in the Summit of the Future described above.
Several alternative news outlets have reported on the UN’s attempt to materialise this pact:
The Federalist – The U.N. Is Planning To Seize Global ‘Emergency’ Powers With Biden’s Support, July 4, 2023 (also via GlobalResearch.ca)
Summit News – Report: UN ‘Pact For The Future’ Seeks Permanent Emergency Powers For ‘Complex Global Shocks’, July 5, 2023
The Western Journal News – Exposed: UN Set to Launch 'Global Shocks' Plan Just Prior to US Presidential Election, July 9, 2023
In a preface to The Federalist article, GlobalResearch notes [with emphasis added]:
“Bear in mind the UN Secretary General is a figurehead, invariably a proxy, who is acting on behalf of by powerful financial interests.
The UN system is in crisis. It is overshadowed by US foreign policy.
Amply documented, there is a US hegemonic agenda behind this proposal. The broader issue is the derogation of the national sovereignty of more than 190 UN member states.”
These are bold assertions for which this author is in total agreement.
There’s no doubt that the Secretary General is indeed a puppet taking orders by those who really run the United Nations, namely the “powerful financial interests,” or International Banking Cabal as I call them.
The Federalist article observes that the Biden Administration supports the UN’s proposal as well as the Emergency Platform (which was described earlier in this post). They add that if the emergency platform is approved, “the United States as we know it could cease to exist.”
GlobalResearch further notes that “there is a US hegemonic agenda” behind this push that is attempting to usurp the national sovereignty of all of the UN’s 190 member states. While this claim is debatable, it does yield merit; for, the United States armed with its intelligence agencies and military might do appear to want to preserve their dominant global position as we are approaching this Fourth Turning and nearing the end of the U.S. dollar system – all of which I have outlined in Part 1 of this series.
Interestingly, the Western Journal article affirms that the UN proposal would begin September 2024, a mere two months before a highly anticipated general election in the U.S.
As Biden’s approval rating continues to dive along with the establishment’s disdain for the overall front-runner Donald Trump, coupled with the fact that it would be difficult to once more place their desired puppet in the Oval Office for 2024, it certainly would be convenient for the powers-that-be who control the United Nations to indeed bring about a global shock in order to activate special measures which could conveniently suspend the election.
Again, this may come across as pure speculation. However, given all that has is being pushed by these supranational entities in the UN, WHO, and WEF, it would certainly come as no surprise; for, a tremendous amount of posturing and effort has already been invested by these actors in order to consolidate their power to secure their New World Order.
A global cyber attack (or even an alien invasion) would undeniably serve their purpose.
Time will certainly tell.
3. The Next Crisis: A CYBER ATTACK
Fool’s Overture
Before explaining the next crisis they are scheming which will most likely be thrust upon us, we must first understand how these things usually happen.
I’ve labelled this introductory section Fool’s Overture, a signature song by British rock band Supertramp back in the late 1970s which warns us not to be too complacent – as individuals, and collectively as a society.
History teaches us that great horrors such as world wars occur when society becomes too ignorant and complacent.
Musically, the song is quite poignant for when you listen to it, it’s almost as if every single cell in your body will vibrate to its soulful quality.
As I mentioned in Part 1, to bring about a major societal shift, some kind of serious catalyst is required.
The example I gave was that of 9/11. The powers that be knew they couldn’t just introduce and implement vast security and surveillance apparatus upon Americans, for they would resist. Hence, they needed an event that would change this mindset. And boy did they ever concoct one!
The choice stratagem to employ is one that has been used for millennia, namely the Hegelian Dialectic – better known as PROBLEM-REACTION-SOLUTION. David Icke has summarised the concept and process quite well.
The Mark of the Beast
As I’ve explained in Part 1, their ultimate goal is to bring about a global Central Bank Digital Currency (CBDC) that is programmable money which they fully control.
There would be no more cash or coin to transact privately.
Consequently, the amount of power and control they would get from a global CBDC would be incredible.
But the only way they can actually pull off a Global CBDC would be with an integrated Digital ID system whereby each and every citizen would be connected.
Many, including myself, have referred to this as the Mark of the Beast. Consult Part 4 of my Covid-19 – Holocaust Comparison series for more on the subject.
In other words, every citizen around the globe would have a Digital ID that can biometrically identify themselves.
This ID could be used for national identification, air travel, banking, paying taxes, determining one’s social credit score (like in China) and so on. Without it, one would have great difficulty in functioning normally in society.
More importantly (for them), having every citizen identifiable and traceable through a Digital ID would provide them with a means to cut them off from the banking and financial system, international travel, and even the internet.
Little room would be left for dissenters, those opposing lockdowns, or those in opposition to prevailing narratives by governing forces which the cabal control.
Furthermore, they could easily impose restrictions such as climate lockdowns which have already been trial-runned in places such as in Oxfordshire in the United Kingdom.
They tried to implement a Digital ID system before and during the Covid-19 Pandemic with Bill Gates’ ID 2020 project. The project entailed leveraging vaccination as an “opportunity” to establish digital identity for citizens in Bangladesh. They seem to almost always trial-run these programs in third-world countries where citizens are less likely to resist.
Other efforts to create Digital IDs and tie them to vaccine passports were attempted around the globe, including in “first-world” countries in G20 nations.
So, now it is time to see how this will all unveil as per the Problem-Reaction-Solution model they will utilise.
STEP 1: Cyber Attack (PROBLEM)
Pretty much everything now functions digitally.
Governments, businesses, organisations, and individuals rely on computer systems and networks for efficient and effective operability.
Without them, we would be returning to methods and lifestyles of the 19th century.
A cyber attack will be the catalyst by which the powers-that-be will bring upon the “need” for a Digital ID.
What will the Cyber Attack look like and entail and what Problems will it bring about?
A large scale (global) cyber attack would likely be characterised as follows:
A shutdown of the electrical energy grid (for a prolonged period);
A total shutdown of the financial system (banking, ATMs, trading, etc.);
A halt in the credit and other financial markets;
A breakdown in the operability of global and domestic supply chains;
A shutdown of the internet (email, online banking, social media, etc.);
A halt in international trade;
A major reduction in health care services (hospitals, surgeries, medicines, etc.)
The near absence of news reporting and dissemination;
A halt in international air travel;
The imposition of martial law, emergency measures, curfews, and lockdowns (to prevent chaos, looting, and the like);
Deployment of military units to help manage and police the situation;
Coordination between country leaders to mitigate the calamity.
STEP 2: Societal Chaos Ensues (REACTION)
Needless to say, the characteristics described above would bring about a tremendous amount of anxiety, despair, and destruction to societies across the world.
Businesses such as supermarkets, pharmacies, and retail stores would be largely disrupted.
Services such as hospitals, emergency services (police, ambulances, fire-fighting units), telephone and cellular networks, 9-1-1 calls would become noticeably constrained, if they work at all.
As for online services, people can barely be removed for a single day from their social media accounts and from the internet altogether.
People will lose their ability to communicate with most of their friends and loved ones, creating a tremendous amount of anxiety and hopelessness.
Water and food supplies, along with basic necessities (such as medicines, toilet paper, diapers, etc.) will become scarce and much harder to come by.
People will find themselves unable to transact in the absence of access to cash machines and digital payment mechanisms.
Can you just imagine the level of frustration individuals will experience?
People would come to realise how dependent they were on electricity and digital networks with all the services and conveniences they provide.
They would also grasp how ill-prepared they are to deal with such tragedies. This may be quite different, however, for those who have prepped for such kinds of catastrophic events.
The only means people would have to show their anger and disapproval would be to mobilise towards their governments, practically begging them to fix the problem ASAP, for it would all be totally unacceptable to them.
Governments at all levels – municipal, state/provincial, and national – would have to draw upon or devise mitigating plans and strategies, and somehow communicate them to the broader public.
With what I’ve just described above, it is not too difficult to contemplate just how much chaos and devastation could ensue following a major cyber attack which would paralyse the systems societies have relied upon on for the better part of the last four decades.
Which other global catastrophe apart from a thermonuclear exchange would bring about such destruction and despair?
That is why I am convinced the cyber attack route is the one they will choose to bring about the New World Order they’ve been lusting about for centuries.
STEP 3: Mandatory National Digital IDs (SOLUTION)
The solution offered by governments (dictated by their masters, the global cabal) will likely entail means by which security and confidence can be restored in online systems and other critical infrastructures (such as those related to energy, finance & banking, government services, etc.)
Mainstream news outlets would be instructed to repeat these mantras of [much needed] security and [the restoration of] confidence over multiple broadcasts (once the power is restored and the problem has been identified, of course).
And this will all be accomplished through the imposition of Digital IDs.
They may not make them mandatory at first; but, those who do not submit to getting them will be shut out of a range of [re-designed] services, leaving them as societal outcasts.
While the above three steps (Problem-Reaction-Solution) may seem far-fetched, the following parts of this post should shed light as to their overall likelihood, and how the powers-that-be are actually hard at work masterminding this particular plan.
4. Cyber Polygon
Image Source: The Sociable
While the UN is hard at work creating the blueprint, framework and emergency protocols necessary to “deal with” a global shock such as a cyber attack, it is the World Economic Forum, or WEF that is preparing its designated private-sector participants to carry out the actual false flag attack.
They have been preparing this for years.
A big part of those preparations have been performed through a simulation called Cyber Polygon.
Before diving into Cyber Polygon, it is important to note that those behind it consist of some of the same actors who prepared Event 201 (Bill Gates and the WEF) which was a global coronavirus outbreak simulation that was held in October of 2019 – merely a few months before the actual coronavirus (Covid-19) pandemic took place. For more on Event 201, consult Part 3 of my post The Covid-19 – Holocaust Comparison.
What is Cyber Polygon?
According to its official website (https://cyberpolygon.com/), Cyber Polygon is an international cybersecurity event aimed at increasing global cyber resilience. The event combines:
online conference with the participation of senior officials from global organization
technical training on cybersecurity for corporate teams
expert talks featuring leading experts in practical cybersecurity
Its stated strategic goals include engaging the management of international organizations and corporations in cybersecurity dialog, among other goals.
It has the support of none other than the International Criminal Police Organization, more commonly known as INTERPOL which is an organisation that facilitates worldwide police cooperation and crime control and has no less than 195 member states.
Cyber Polygon’s two principal partners consist of two Russian private firms, namely BI.ZONE and Sber (formerly Sberbank), the largest bank in Russia, Central and Eastern Europe, and one of the leading financial institutions worldwide.
So far, Cyber Polygon has held training and simulation events for:
2020 (watch the full event video here and read the results here);
2021 (watch the full event video here) and read the results here);
The WEF’s involvement
The World Economic Forum (WEF) has been a key facilitator and contributor to Cyber Polygon. For many years already, the WEF has posted many articles on cybersecurity which is a key topic in their agendas. Here are some related WEF articles and sources on the subject:
Systemic Cybersecurity Risk and role of the Global Community: Managing the Unmanageable, Briefing Paper, November 2022
Why we need global rules to crack down on cybercrime, Jan. 2, 2023
see also A UN treaty on cybercrime en routeThe US has announced its National Cybersecurity Strategy: Here’s what you need to know, March 9, 2023, see also The White House – National Cybersecurity Strategy (March 2023)
What you need to know about cybersecurity in 2022, Jan. 18, 2022, see also Global Cybersecurity Outlook 2022, Insight Report, January 2022
Systemic Cybersecurity Risk and role of the Global Community: Managing the Unmanageable, Briefing Paper, November 2022
Fractured Identity: A Prescription for Mending the Identity Ecosystem, Briefing Paper, September 2021
4 principles for securing the digital identity ecosystem, Mar 18, 2021
To Prevent a Digital Dark Age: World Economic Forum Launches Global Centre for Cybersecurity, Jan. 24, 2018
While there is a lot that can be sifted through in the links above, what we must pay most attention to is twofold: global rules and response and Digital ID systems.
The article Why we need global rules to crack down on cybercrime from earlier this year, provides us with some valuable insights. The article states at the very top “The cost of cybercrime could reach $10.5 trillion annually by 2025.” This is obviously to demonstrate the “severity” of the problem and its [supposed] cost to societies.
The article also calls for “international rules” to mitigate cybercrime which includes a cyber breach reporting platform at PricewaterhouseCoopers (PwC) – a mammoth international accounting and consulting firm, and an EU-wide Directive on cybersecurity.
Two sources deal with Digital IDs.
The first deals with established and developing norms as they related to authenticating one’s identity – such as during international travel, including by biometric means. The article was written by Colin Soutar, the Managing Director, Cyber Risk, for Deloitte – another prominent international accounting and consulting firm.
And the second one, Fractured Identity: A Prescription for Mending the Identity Ecosystem, is particularly revealing. Here are some key excerpts [with emphasis added for relevancy]:
"Digital identity – the representation of a unique individual engaged in a digital transaction – is central to managing fraud risk and improving accessibility of online transactions." (page 3)
[perceived PROBLEM – next three passages:]
"Globally, digital identity is fragmented. Historically, countries have defined their own digital identity requirements, data, attributes and policies..." (page 3)
"This localization is a substantial challenge, with governments and private sector organizations executing on disparate identity schemes across geographies to enable relying parties to have confidence in a credential or attribute." (page 3)
"Passports have always had a high level of trust and standardization but there is not yet a digital equivalent. The idea that each of these disparate localities will align on a single paradigm is flawed. Instead, to coalesce an international ecosystem, specific roots of trust can be established to enable technical and policy interoperability between and among digital identity systems." (page 3)
[GLOBAL ID]: "A strong, global identity ecosystem has the potential to improve digital transactions for government, commercial organizations and individuals:" (page 4)
[INDIVIDUAL & BIOMETRICS]: "Individuals: Digital identity can improve access for individuals to a variety of resources while, in many cases, also impowering [sic] them to manage their own identity and attributes. Instead of the 100+ accounts they deal with now, they would have one strong identity protected by multifactor authentication – biometrics, mobile device, token, or all the above – to access services. In the world of a global identity ecosystem an individual could potentially use this credential to book an airline ticket, get through airport security, pass through customs and border arrivals, and then check into a hotel." (page 4)
[PROBLEM/OBSTACLES]: “A number of obstacles must be overcome to enable a globally interoperable digital identity ecosystem. This paper will look at those blockers and help guide policy-makers in how they could overcome them.” (page 4)
“Conclusion:
Opportunities exist to mend the fractured global identity ecosystem. As the world takes its first steps out of the COVID-19 pandemic, it is a good time to look at the problems with digital identity and create a plan for mending the disparate systems in existence today.” (page 12)
We can clearly see what they are trying to accomplish with this briefing paper. They want to bring about the establishment of a standardised and global “digital identity ecosystem” whereby individuals will be required to submit biometric information in order to authenticate their identity, proving who they are.
Without this global biometric Digital ID, individuals wouldn’t be permitted to book hotel rooms or flights, and get through airport security and customs & border checkpoints.
It couldn’t be clearer that this is what they are seeking.
A big part of the WEF’s playbook involves fomenting fear (as was the case during Covid-19).
Apart from the alleged $10 trillion yearly losses due to cyber crimes, they like to instill a sense of unease in other areas. The following video states that a global cyber attack would be 10 times worse than the Covid-19 Pandemic:
“A single day without the internet would cost our economies more than 50 billion US dollars, and that is before considering the economic and societal damages should these devices be linked to essential services, such as transports or healthcare.”
The WEF often likes to utter these kind of fear-mongering statements. US$50 billion per day without the internet. Really? Frankly speaking, it just sometimes seems like they pull these numbers out of their arses, seldom citing where such estimates come from.
Notice that the Comments section for all videos posted on the WEF’s official YouTube channel are always off. They obviously do not want people countering their claims and pointing out their nefarious plans. For an organisation that purports to be doing good and promoting fascist public-private partnerships, they are not being transparent.
Let us now have a look at the various Cyber Polygon exercises and how the WEF has been involved in the process.
Cyber Polygon 2020 edition
"We all know, but still pay insufficient attention to, the frightening scenario of a comprehensive cyber attack, which would bring a complete halt to the power supply, transportation, hospital services, our society as a whole” — Klaus Schwab (Executive Chairman of the WEF, Cyber Polygon 2020"
Klaus Schwab, Executive Chairman of the World Economic Forum provided the Welcoming Remarks for Cyber Polygon in which he stressed that a global response and platform would be needed to address the “systemic cybersecurity challenges.”
“...Requires a global response with strong public-private cooperation...the WEF launched in 2018 the Center for Cyber Security... to offer a global convening platform for governance large corporations and civil society to address the systemic cybersecurity challenges and find joint solutions. It is obvious that governments have to play a leading role in securing cybersecurity...and improve our preparedness for potential cyber pandemic...We need to take decisive action in preparing. I'm glad that Cyber Polygon is one of the great initiatives that address the need for building capabilities that enhance global cyber resilience and preparedness fighting against cyber crimes and cyber attacks.”
Cryptocurrency expert Guy from the Coin Bureau provided a very good overview of Cyber Polygon 2020:
In the video, Guy mentioned that he provided a link to an excellent article on the subject (which was written by acclaimed investigative journalists Johnny Vedmore and Whitney Webb). The article, titled From “Event 201” to “Cyber Polygon”: The WEF’s Simulation of a Coming “Cyber Pandemic” also provides an excellent overview of Cyber Polygon and includes profiles of some of its key participants.
One of those participants is Herman Gref, a member of the Board of Trustees of the World Economic Forum and Sberbank’s CEO who uttered the following warning at the event [with emphasis added]:
“We all know, but still pay insufficient attention to, the frightening scenario of a comprehensive cyberattack which would bring to a complete halt to the power supply, transportation, hospital services, our society as a whole. The COVID-19 crisis would be seen in this respect as a small disturbance in comparison to a major cyberattack. We have to ask ourselves, in such a situation, how could we let this happen despite the fact we had all the information about the possibility and seriousness of a risk attack. Cybercrime and global cooperation should be on the forefront of the global agenda.”
Vedmore and Webb added the following salient points in their critique:
“The inevitable collapse of the global banking system, resulting from the off-the-charts corruption and fraud that has run rampant for decades, is likely to be conducted through a controlled collapse, one that would allow wealthy bankers and elites, such as those that participated in Cyber Polygon, to avoid responsibility for their economic pillaging and criminal activity...
A massive cyberattack, such as that simulated at Cyber Polygon 2020, would allow faceless hackers to be blamed for economic collapse, thus absolving the real financial criminals of responsibility.
Furthermore, due to the difficult nature of investigating hacks and the ability of intelligence agencies to frame other nation states for hacks they in fact committed themselves, any boogeyman of choice can be blamed,”
I wholeheartedly agree with their assessment. The elite banksters need a means by which they can collapse (and rebuild) the global financial system whereby they can avoid scrutiny and blame for their years of looting the global public through increases in money supplies that have caused rampant inflation which represents a drastic reduction in the purchasing power of our respective national currencies. A “massive cyberattack” indeed fits the bill and is, evidently, the overall premise of this post.
When they note “due to the difficult nature of investigating hacks,” it adds to the viability of the simulation becoming fait accompli; for, the general public is simply not aware about the complexities involved with cybersecurity and will just likely go along with government and mainstream media’s explanations on such matters.
Moreover, for the latter part of their statement in which intelligence agencies will likely blame a certain nation state – the boogeyman – for the attack, it will be textbook CIA procedure (as it has been for decades). I will talk more about this aspect in section 6 of this post.
The reader can go through the 4+ hour video about the 2020 Cyber Polygon simulation exercise, or read through its final report, but we can leave it at that for now.
Cyber Polygon 2021 edition
The global cyberattack simulation was repeated in 2021.
Here is a promotional video posted by their major partner BI.ZONE on their YouTube channel with, in WEF-style, Comments turned off:
The general focus of the 2021 edition was concerned with simulating attacks on corporate – supply-chain – financial/banking infrastructures.
The results report indicated that the areas of discussion for this edition centered around the following:
“...ecosystem integrity, supply chain security, financial system stability in the age of digital currencies, international cooperation in cybersecurity, the protection of children online and much more.”
“Top officials from INTERPOL, UNICEF, the International Committee of the Red Cross, ICANN, Visa, Mastercard, IBM, Microsoft and other international organisations took part in the discussions,” the report also indicated.
ICANN is a noteworthy participant, for it is a global authority that manages internet domains (IP addresses) and helps to ensure the “secure operations” across the internet. In terms of internet security, ICANN has a lot of power since it can determine Reputation Block Lists, or RBLs which are “lists of Domain Names, Universal Resource Locators (URLs), and/or Internet Protocol (IP) addresses that have been identified as posing security threats.” Their blog post Reputation Block Lists: Protecting Users Everywhere from Nov. 1, 2017 focuses on cybercrime and cyber threats.
While global internet security is indeed important, ICANN’s participation at the WEF-led event is somewhat worrisome; for, if their top management somehow gets compromised, they can become impelled to acquiesce to banning certain parties from the internet.
IBM and Microsoft are almost always present in these kinds of events.
As for Visa and Mastercard, some of their top executives appeared together in a panel discussion titled New World – new currency which focused on digital currencies, digital identity, and how to make the financial system more “resilient.”
An article published in Global Research by author Tim Hinchliffe highlighted three key trends that emerged and became apparent in the Cyber Polygon 2020 and 2021 exercises:
Governments Will Inevitably Move Towards Digital Identity Schemes
‘Fake News’ is a Digital Pandemic & the Majority of Citizens Are Incapable of Thinking Critically
Trustworthy Public & Private Partnerships Will Need To Be Strengthened
The first trend – governments moving towards Digital Identity Schemes, is perhaps the most important.
“Digital identity is a major component of the WEF’s great reset agenda as it relates to transformative technologies powering the Fourth Industrial Revolution,” notes Hinchliffe.
“A digital identity keeps a record of everything you do online, including what you share on social media, the websites you visit, and your smartphone’s geolocation, and it can house all of the credentials you would normally find in a physical wallet, such as your driver’s license, insurance card, and credit cards.”
To this point, the author noted a very important passage which figured in the Executive Summary of the 2018 WEF report titled Identity in a Digital World A new chapter in the social contract:
“Our identity is, literally, who we are, and as the digital technologies of the Fourth Industrial Revolution advance, our identity is increasingly digital. This digital identity determines what products, services and information we can access – or, conversely, what is closed off to us.”
They state that our digital identity determines which products, services, and information we can access – which is almost everything that we need to function normally in society. They also clearly imply that all of these can become “closed off to us.”
Who the hell are they to determine this? When did we ever elect them to dictate such a monstrous and obnoxious display of gall?
The problem, however, is that they are right in the sense that access to products, services, and information (i.e., the internet) could indeed become cut off should a Digital ID – a global, or even national one – come to fruition.
Programmable money (CBDCs) would figure among these tools of tyranny.
The article also points to a November, 2020 WEF document which further outlines the digital identity scheme they wish to materialise:
Digital Identity infographic. Source: World Economic Forum (archived here).
As can be seen in the image above, they want to link digital identity with pretty much everything.
Needless to say, the sheer amount of power and abuse that could be used against individuals with such a national or global digital identity scheme is exactly what these powers-that-ought-not-be seek and would use for total control on populations, even though none of these WEF cronies, members, and participants were ever elected by we the people.
Moreover, a Digital ID tied to a CBDC would further ensure that dissenters (or journalists like myself) could easily be shut off financial systems and largely unable to transact normally.
The Israeli Cyberattack Simulation (against the Global Financial System)
Professor Emeritus Michel Chossudovsky who is also the Founder and Director of the Centre for Research on Globalization (CRG) based in Montreal noted early last year that Israel had also conducted a simulation of a cyberattack against the Global Financial System in 2021.
In that report, Chossudovsky observed that the objective of the exercise, titled “Collective Strength” remains unclear, and that apart from members of 10 participating nations, senior staff members from the IMF, the World Bank and the Bank for International Settlements (BIS) were also present.
Surprise, surprise.
“The unique and groundbreaking exercise held today showed the importance of coordinated global action by governments together with central banks in the face of financial cyber threats,” Greenberg said. (Times of Israel, December 9, 2021)”
Unlike the Cyber Polygon exercises which are somewhat more broad-based, this particular simulation dots all the i’s and crosses all the t’s. That is to say, it covers all the major aspects that such a cyberattack on the financial/banking system (possibly including the power grid) would have on society, businesses, and individuals.
The simulation saw “attacks” which impacted global foreign exchange (currency exchange and trading), bond market [disruption], liquidity (credit), and “integrity of data and transactions between importers and exporters” (which means a major disruption in supply chains).
In addition, the Israeli simulation covered the possible aftermath of “fake news” being propagated which would cause “chaos in global markets and a run on the banks.”
A run on the banks occurs when depositors get nervous and flock to their respective banks to withdraw all their funds. Such events have occurred multiple times in history, usually with devastating consequences, leading to bank failures.
The linked Reuters article about the simulation also noted the following [with emphasis added]:
“The participants discussed multilateral policies to respond to the crisis, including a coordinated bank holiday, debt repayment grace periods, SWAP/REPO agreements and coordinated delinking from major currencies.”
A “bank holiday” is a cryptic oxymoron which means that a bank can completely shut its doors, its ATMs, and online services for a certain period that can last days, if not longer.
A “coordinated bank holiday” implies that many banks would shut down at the same time.
What is not mentioned in the quote above, but is usually associated with bank holidays are bank bail-ins (which are not to be confused with bank bail-outs whereby governments allocate funds to replenish bank reserves to keep it solvent and operational).
Bank bail-outs occurred during the 2007-08 Financial Crisis.
Since that financial crisis, many countries around the world have adopted bank bail-in legislation, permitting them to essentially steal funds from depositors in the event of a bank crisis.
The United States (see here, here, and here) and Canada (see here, here, here, and here) figure among many countries that have such bail-in legislation.
In 2013, bank customers in Cyprus saw their bank appropriate (steal) money directly from their accounts in order to keep the bank solvent and operational.
Bank of Cyprus customers lineup on March 28, 2013 after they reopened for the first time since March 16. Images source: CyprusMail.
As I have explained in Part 1, the current monetary system (and, inherently, the financial system) is not sustainable and is on its last legs.
There is too much debt to be re-paid and too many liabilities on the books (e.g., Social Security’s unfunded liabilities in the United States, sing to the tune of $96 trillion).
Hence, we can see that they are actively prepping and fostering coordination among central banks around the world for such kinds of “financial cyber threats.”
===> A major global cyberattack could thus serve as a culprit, removing the focus off of the banksters (read International Banking Cabal) themselves and their heinous mismanagement of the global financial system and their decades of looting the citizenry through their inflation and banking shenanigans.
Returning to the article, the seasoned author Chossudovsky also noted that what was contemplated by the Israeli simulation was very similar to the WEF’s Cyber Polygon 2021 exercise which consisted of:
“…A scenario of economic and social chaos involving the disruption of communications systems, the internet, financial and money transactions (including SWIFT), the power grid, global transportation, commodity trade, etc.”
In other words, such kinds of cyberattacks would be all-encompassing, not just affecting financial infrastructures, but also many others.
Furthermore, we can see that supply chains (global transportation and commodity trade) would be largely affected, as would countries’ power grids. This would inevitably lead to shortages of all kinds of goods, including food, as well as substantial price increases.
The latter – power grids – is key; for, a global cyberattack that would knock out countries’ entire electricity infrastructure would, in turn, sow complete chaos on citizens who have become so reliant on this form of energy.
We can thus easily see the stakes at play with all these “cyber pandemic” simulations which WEF Executive Chairman Klaus Schwab said would be “around 10 times greater than what we’ve experienced with the coronavirus [pandemic],” to which he also added:
“We all know, but still pay insufficient attention to, the frightening scenario of a comprehensive cyber attack, which would bring a complete halt to the power supply, transportation, hospital services, our society as a whole.
The COVID-19 crisis would be seen in this respect as a small disturbance in comparison to a major cyberattack.”
The frightening part in his statement is that it is true.
A highly-disruptive cyberattack that would bring down entire infrastructures as described above would indeed wreak havoc on the masses, perhaps creating a major (Biblical) depopulation event in the process – something that they have ramped-up during the Covid-19 scamdemic.
Cyber Polygon 2022 edition
“INTERPOL has been an integral part of the Cyber Polygon since its inception in 2019. This partnership aligns with one of our core pillars of enhancing the capabilities of law enforcement in combating cybercrime, part of INTERPOL’s Global Cybercrime Strategy in support of our 195 member countries. We have no doubt that this year’s Cyber Polygon will provide another important milestone for us all to become more agile and responsive to the ever-evolving cybercrime in the cloud age,”
The above was a statement issued by Craig Jones, Director of Cybercrime at INTERPOL.
International Criminal Police Organization, commonly known as INTERPOL, is an inter-governmental organisation concerned with international cooperation in police matters; it consists of 195 member countries.
While such cross-border policing activities conducted by INTERPOL and its member states is generally a good thing, what is worrisome is its alignment with the United Nations and its UN Agenda 2030, including its Sustainable Development Goals (SDGs).
Part of INTERPOL’s Global Policing Goals web page, with emphasis added in red underlining. Screenshot taken on August 29, 2023.
As is shown in the screenshot image above, INTERPOL does have its Global Policing Goals, in addition to a Cybercrime Global Strategy under their 2022-2025 Strategic Framework.
INTERPOL states the following with regards to its alignments with the UN Agenda 2030 and its SDGs:
“The Global Policing Goals focus the collective efforts of the international law enforcement community to create a safer and more sustainable world for future generations.”
They also include the following graph on their Global Policing Goals page:
If you read through the seven Global Policy Goals, you can easily see that they are precisely aligned with the UN’s SDGs, and primarily with Goal 16 (Peace, Justice, and Strong Institutions). Moreover, the circles with coloured segments on the graph above refer to specific SDGs.
As I have previously outlined in this series and other posts of mine, the UN Agenda 2030 and its SDGs are heavily geared towards stripping away are rights and doing the opposite of what they are purported to accomplish.
This leads me to believe that those controlling the United Nations are also either controlling INTERPOL itself, or at least have partly compromised (weaponised) the institution to further their nefarious agendas.
Sure, many would rightfully argue that as an international policing body, they would figure among essential players in such kinds of simulations as Cyber Polygon. But, the fact that this event is sponsored by the WEF and other questionable actors certainly does not lay credence to this so-called policing organisation and its seemingly benevolent intentions.
For instance, look at INTERPOL’s Goal 7 (Support environmental security and sustainability) from above. Who is to say that they won’t use this as a means help to enforce Climate Lockdowns? If not, then what else do they mean by this specific goal?
I could certainly be wrong. But my instincts tell me otherwise, at least with regards to these specific alignments and associations.
Returning to the Cyber Polygon 2022 event, The Sociable – a technology news blog that covers issues related to the Great Reset, Digital IDs, and CBDCs – emphasised the theme for this edition, namely “digital resilience in the cloud age.”
They add that their cybersecurity training focuses on sectors engaging with cloud services such as: finance, retail, healthcare, transportation, commodities, among others.
The Sociable also notes that according to the Cyber Polygon 2022 concept page, “Security risks are growing, with cybercriminals actively exploiting vulnerabilities in new cloud environments.”
In a follow-up March 30, 2022 article titled ‘History is truly at a turning point, global energy & food systems will be deeply affected’: Klaus Schwab to World Government Summit, the same author, Tim Hinchcliffe highlighted Klaus Schwab’s dire warnings of impending global doom during an address at the World Government Summit held in Dubai.
“We do know that global energy systems, food systems, and supply chains will be deeply affected” — Klaus Schwab, World Government Summit, March, 2022
In his opening remarks, Schwab also concluded that only global collaboration could counter these threats.
The Sociable also noted the following about Russia:
“On March 21, 2022 the White House issued a warning that “Russia could conduct malicious cyber activity” against America’s critical infrastructure “as a response to the unprecedented economic costs we’ve imposed on Russia alongside our allies and partners.””
I will talk more about boogeyman Russia in section 6 below. But for now, we must not underestimate their ability to find a plausible, but nonetheless completely made up, culprit who would be malicious enough to stage a large-scale cyberattack, and for which blame can conveniently and easily be laid upon. They do, after all, still have a lot of unfinished business in Russia.
In a Global Research article from March of 2022, Dr. Joseph Mercola noted that the WEF’s Great Reset globalist plan is “moving forward at lightning speed,” adding the following very important points [with some emphasis added for relevancy]:
“The COVID-19 pandemic was part and parcel of that plan, but to really fulfill the technocrats’ ambitions, a war of some kind is likely needed.
They need chaos, mass casualties and financial chaos in order to create the desperation necessary for people to give up their freedoms and give in to tyrannical control.
The World Economic Forum (WEF) has for years promoted the implementation of digital identification, and ensuring that everyone on the planet has a legal, digital identity [that] is part of the United Nations’ 2030 Sustainable Development Goals.
There’s a big difference between identity and identification.
Identification refers to documents that prove you are who you say you are. A digital identity is NOT merely a form of identification. Your “identity” is who you actually are, and a digital identity will keep a permanent record of your choices and behaviors, 24/7. These data can then be used against you.
The WEF has clearly stated that our digital identity will determine “what products, services and information we can access — or conversely, what is closed off to us.”
Everything Dr. Mercola has stated above is factual and true, as I have thoroughly documented in this series.
Dr. Mercola has been critically outspoken during the Covid-19 Pandemic and has provided us with a tremendous wealth of knowledge. His heeded words, therefore, ought to be taken with unswerving seriousness.
In the article, Mercola also points to another piece in The Exposé in which its author issues the following warning: “Remember: the covid fraud was just the beginning. The conspirators have only just started their campaign to take total control.”
And it is through Digital IDs that they seek to accomplish this “total control.”
And, technically speaking, he is right should the banksters get it as a precursor to their CBDCs.
Mercola expands on this point by referring to the article Your digital identity can be used against you in the event of a great reset in which the author notes the following:
“The idea behind digital identities is simple enough. All the data collected from every online interaction you make with the private and public sectors goes into forming your digital identity.
This data can include your personal:
Search history
Social media interactions
Online profiles
Device location
Medical records
Financial ledgers
Legal documents
And more”
What about Cyber Polygon 2023?
To conclude this section on Cyber Polygon, their website doesn’t seem to indicate that a 2023 event has been scheduled to take place. Moreover, there is next to nothing on the internet about 2023.
It is somewhat odd that they haven’t continued the simulation exercise, for it seemed to have become a yearly event.
Perhaps they no longer wish to project what they are actually planning to carry out.
Another reason might be that since Cyber Polygon was initially mostly led by Russian participants, its popularity may have faded since the Russian invasion of Ukraine.
Finally, what is particularly noteworthy about their last simulation – Cyber Polygon 2022 – has to do with what follows in the next section.
5. Test-Run in Canada? The Rogers Outage
As was reported by The Sociable, the massive internet and cellular communications outage that took place in Canada over Rogers Communications’ networks occurred on the same day (July 8, 2022) that Cyber Polygon 2022 was to take place.
Coincidence?
Though the Cyber Polygon 2022 event was postponed (to a later date) months earlier, it remains quite suspicious as to why the nation-wide outage occurred on that specific day, July 8, 2022.
As Reuters reported a few days later, the outage disrupted nearly every aspect of daily life, cutting banking, transport and government access for millions, also hindering the country's cashless payments system at retailers, ATM withdrawals, and calls to 911’s emergency services.
Let us, then, scrutinise the major outage that knocked out a quarter of Canada’s internet traffic which affected 11 million users (over a quarter of the population), and was the largest internet outage in Canadian history.
Even though Rogers Communications blamed the outage on a maintenance upgrade which caused routers to malfunction, Doug Madory, the Director of Internet Analysis for Kentik (a network analytics firm specialising in internet infrastructure analysis) debunked some of the claims.
Technically Speaking
Though these matters are of a very technical nature, I will try to simplify them as much as possible to enable the reader to gain a general understanding of the issue at hand.
Feel free to skip this subsection if it is beyond your pay grade.
Madory contends that the suspension of internet traffic was not caused by BGP (Border Gateway Protocol) issues but that these were mere symptoms of the problem.
In laymen’s terms, BGP is an important protocol that governs the traffic through the internet, kind of like an Air Traffic Controller directs planes to proper runways at airports.
Internet traffic to Rogers (AS812) from July7, 2022 to July 10, 2022. Image source: Kentik.
The internet is basically a network of networks.
Rogers network (which is ascribed the code AS812) enables its subscribers to connect to the internet and helps to manage the flow of traffic to and from it (emails, web browsing, Zoom calls, etc.)
The way data flows across the internet is by something that is called BGP routing.
Each network, like the Rogers one, is part of a larger system of packet routing (all data transmitted over the internet are comprised of packets).
If there is a disruption in this “piping” then the flow of data gets cut (similar to a water pipe freezing on a frigid winter night, obstructing the usual flow).
In his analysis of Rogers’ outage, Madory notes the following:
“Initial analyses of the outage reported that Rogers (AS812) couldn’t communicate with the internet because its BGP routes had been withdrawn from the global routing table. While a majority of AS812’s routes were withdrawn, there were hundreds of IPv4 and IPv6 routes that continued to be announced but stopped carrying traffic nonetheless. This fact points more to an internal breakdown in Rogers’ network such as its interior gateway protocol (IGP) rather than their exterior gateway protocol (i.e. BGP).”
Basically, he is noting that the problem was more of “internal plumbing” at Rogers than its connection to the broader internet network.
Moreover, he noted that what was strange in Rogers’ outage is that BGP routes had actually remained available [for data transmission through the Rogers network] yet traffic did not flow.
Cloudfare, an internet security firm, also noted that the problem was more of an internal nature [to Rogers’ network system].
Cloudfare also notes that the Rogers outage was not caused by BGP updates, and also remarked the unusual occurrence of the removal of prefixes (which are groups of IP addresses) to their network. Without proper handling of such prefixes, internet traffic cannot flow properly through the network.
One could ask whether these prefixes were deliberately removed or somehow halted from Roger’s internal network.
What’s more, Madory further noted the fact that Rogers’ Fido mobile service reported having no bars of service during the outage which was a “head-scratcher.”
“What is a common dependency that would take down the mobile signal along with internal routing?” he further asks.
Thoughts on the Rogers outage
While it is nearly impossible to know for sure what exactly occurred on with Rogers’ network, the public statements issued by Rogers don’t align with the analyses and technical abnormalities as described above.
It could, therefore, suggest some kind of foul play.
Furthermore, it is certainly possible and feasible that technical changes were made to their network, such as the blacklisting of certain IP addresses in preparation for the future.
Stated differently, such kinds of “upgrades” could be used to block traffic flows to and from certain websites/domains.
“With the recent developments in cyber security, organizations are increasingly relying on IP blacklisting to protect their networks,” notes Atatus.
Such changes are often justified for cybersecurity purposes – and rightfully so. But, at the same time they can easily be used and abused to unjustly ban certain parties from accessing the internet, as has been the case with persons who have been “debanked” by banks and financial institutions without due legal process.
The troubling trend, unfortunately, seems to be increasing with time.
While IP blacklisting is not a bad thing in and of itself (like to protect us against spammers and scammers), it could also be used as a weapon against dissenters or those providing information that is deemed “dangerous.” This was the case with NaturalNews.com who got blacklisted by social media giant Google and others several years back.
There’s perhaps no better example of IP blacklisting than what we see with China’s Great Firewall whereby something like 80% of internet sites are inaccessible within the country.
Living in China for 13 years was nearly impossible for me without the use of a VPN (an application software that allows accessing the internet from external addresses) to be able to access the internet.
Internet providers such as Rogers can easily include blacklists in their network configuration to ban certain parties from accessing or appearing on the internet. They can be instructed to do so by relevant authorities, and would have to comply, as would be the case with all Internet Service Providers (ISP).
Time will tell how this particular form of “digital exclusion” will evolve in the coming years and what part network operators such as Rogers, Bell, Verizon, T-Mobile, AT&T, et al, will play in the matter.
Another outlier about the outage was the fact that Marco Mendicino, Minister of Safety at the time immediately dismissed the possibility that the Rogers outage was due to a cyber attack. He stated this on the very same day of the outage even though a forensic analysis for such kind of highly technical event would normally take days, if not weeks. Did he know something that we didn’t?
Lastly, the Rogers outage in Canada – whether done deliberately or not – served as a test-run for how the greater population would be impacted by the suspension of internet and other online services as well as a gauge to their reactions.
As was referenced in videos from some of the news articles listed above, the masses found it quite challenging to go about their routines without cell and internet coverage. And that was for practically less than one day. Imagine the same kind of event, but without access to electricity. It also highlighted the case for having the option of using cash, for many were left unable to pay for goods and services during the outage.
Note: Special thanks must be granted to Gabriel Wilson from Libre Solutions Network for his assistance in helping me understand the technical nature of Rogers’ outage and how internet traffic works. Gabriel writes extensively about online censorship and provides many excellent resources and tools to counter such tyranny. Be sure to check out his Substack articles such as the excellent Tools of the Technocracy (which also contains a post on Internet Shutdowns), Cybergeddon: ISP-level de-platforming, and Operation: Beehive which provides excellent information and more secure and private substitutes to mainstream platforms and apps (i.e., alternatives to Facebook, Google, YouTube, Microsoft Office, etc.) such as switching.software.
6. The Cyber Boogeymen (Russia & China)
As was briefly touched upon in section 4 above about the Cyber Polygon cyberattack simulation, a country such as Russia can easily be blamed for a large-scale cyberattack.
It is no secret that they U.S./NATO Military-Industrial-Complex alliance has long counted on perceived threats from certain nation states to justify their mammoth military expenditures and illegal invasions (think Iraq and Libya as prime examples).
As for Russia, NATO and the U.S. been at it for decades.
In one of my most viewed posts – Ten Inconvenient Truths about Ukraine largely ignored by the MSM – I outlined how the U.S. and NATO had purposely expanded their military intrusions near Russia’s border and how they conducted a coup in the Ukraine in 2013-2014 in order to foment chaos so that they could install a U.S.-friendly government in that country.
In a separate article, I outlined how the U.S. and Canada had vilified Russia and passed laws (the Magnitsky acts) to sanction and punish Russia which were entirely based on lies and deception.
In addition, I have also exhibited how the U.S., NATO, and NATO Canada have been employing 5th Generation Warfare tactics online in order to vilify Russia and garner support for the Ukraine. This extensive psychological operation conducted against the global citizenry have served to solidify the notion that “Russia is bad” and “Putin is an evil tyrant killer.” And, sadly, the non-discerning masses have swallowed the rhetoric hook, line, and sinker. In other words, this brainwashing and mind control operation has proven to be a stunning success.
Accordingly, these types of operations makes labelling Russia as Enemy Number One child’s play.
Over the last several years, the U.S. Government has blamed various cyberattacks which targeted U.S. interests for which some were legitimate, but many were complete fabrications, particularly with regards to election meddling and the whole Russiagate ploy against former President Donald Trump.
Addendum 2023-09-01: Back in late 2016, it was reported by WashingtonsBlog that despite the Democrats having blamed Russia for the Democratic National Committee (DNC) hack (like was reported by the CIA/CFR’s mouthpiece the New York Times), it was actually attributable to a leak from within the party.
Moreover, the same blog reported that according to high-level American Intelligence officials, the allegations of hacking were baseless. These officials consisted of Veteran Intelligence Professionals for Sanity (VIPS). Mountains of evidence were provided to demonstrate that Russia was not to blame for this hack, but was rather framed for it. The previous article pointed out the following:
“A leading IT think tank – the Institute for Critical Infrastructure Technology – points out:
Malicious actors can easily position their breach to be attributed to Russia. It’s common knowledge among even script kiddies that all one needs to do is compromise a system geolocated in Russia (ideally in a government office) and use it as a beachhead for attack so that indicators of compromise lead back to Russia.”
A few months later (in March of 2017), Wikileaks had also published ‘Vault 7: CIA Hacking Tools Revealed’ that exposed a huge arsenal of hacking tools, including stolen ones from Russia which could be used to simulate a hack that seems to originate from that state and blame them; here is the entry for UMBRAGE as exposed by Wikileaks which does just that [emphasis added]:
“UMBRAGE
The CIA's hand crafted hacking techniques pose a problem for the agency. Each technique it has created forms a "fingerprint" that can be used by forensic investigators to attribute multiple different attacks to the same entity.
This is analogous to finding the same distinctive knife wound on multiple separate murder victims. The unique wounding style creates suspicion that a single murderer is responsible. As soon one murder in the set is solved then the other murders also find likely attribution.
The CIA's Remote Devices Branch's UMBRAGE group collects and maintains a substantial library of attack techniques 'stolen' from malware produced in other states including the Russian Federation.
With UMBRAGE and related projects the CIA cannot only increase its total number of attack types but also misdirect attribution by leaving behind the "fingerprints" of the groups that the attack techniques were stolen from.”
Put simply, the CIA can create “fingerprints” that genuinely appear to originate from certain places, in this case Russia.
The above demonstrates that members of the U.S. Intelligence Community – particularly the CIA has many tools at its disposal to frame other parties or nations for hacks or cyberattacks.
These were tools that existed prior to 2017; so, imagine what other [covert and classified] capabilities they now have at their disposal.
As such, it is not very difficult to observe that Russia, China, or any other actor can have blame cast upon them for a malicious attack.
/End of Addendum 2023-09-01
Last year, the Biden Administration has ramped-up its rhetoric with regards to potential cyberattacks from Russia.
Here is an excerpt from a White House Statement by President Biden on our Nation’s Cybersecurity [with emphasis added]:
“I have previously warned about the potential that Russia could conduct malicious cyber activity against the United States, including as a response to the unprecedented economic costs we’ve imposed on Russia alongside our allies and partners. It’s part of Russia’s playbook. Today, my Administration is reiterating those warnings based on evolving intelligence that the Russian Government is exploring options for potential cyberattacks.”
There is no doubt that countries like Russia, China, and North Korea do indeed have formidable cyber warfare capabilities.
This, therefore, makes it quite plausible to believe such statements. But, at the same time, a lot of it could just be rhetoric and posturing to lay future blame on what could turn out to be a false flag attack.
The U.S. has conducted many of these types of false flags attacks over the years – with many that were facilitated by the CIA. So, it would certainly come as no surprise that yet another one could be fabricated with blame laid on a nation like Russia, or China.
In recent years, the U.S., Canada, and other Western nations have also vilified China as a potential threat.
While China does indeed have extensive cyber warfare resources and has conducted many cyberattack-style operations against many countries in recent years, one that would entail a major attack against another nation would seem highly unlikely.
Even so, China could serve as an ideal culprit for a massive cyberattack given its capabilities and the fact that most Western nations’ citizens know almost nothing about China.
Hence, they could easily be blamed as a barbarian state that “is out to get us” and unseat the United States as the world’s hegemon.
The U.S. knows that China is a formidable economic and military superpower – one that is armed with a substantial nuclear arsenal. As such, a full-on military conflict with China is very unlikely, even with its stance on the Taiwan issue.
The United States’ desire to weaken China in any way it can remains, and ought to be seriously considered.
To conclude this section, should a massive global cyberattack occur – even a contrived, false flag one would require a culprit with both the means and motivation to carry out such a damaging attack.
The global masses would have to be somewhat convinced about this so-called new and cruel enemy. And currently, no other party other than Russia or China currently fits the bill.
7. Post-Cyber Attack Era
A large-scale, global, cyberattack would create a new era that is similar to the post-9/11 one.
Since the fateful events of September 11, 2001, citizens around the globe have been subject to an unprecedented level of surveillance and control. Many of our rights have been stripped away from us, all in the name of the so-called “war on terror.”
When you think about it, how many real large-scale terrorist events have occurred since then?
Moreover, the number of heightened security measures at airports and across borders have made visiting other countries a pain in the ass.
Governments have always took it upon themselves to “never let a good crisis go to waste.” They capitalise on such kinds of events to pass more yet more encroaching legislation that increases their power while incrementally removing our fundamental rights and freedoms.
Accordingly, it is to be expected that following a global cyberattack, the introduction of new legislation (which will have likely already been written, like the U.S. Patriot Act) which would deprive us of even more rights and freedoms.
In the case of legislation following a global cyberattack, we could easily expect the introduction of mandatory Digital IDs which would serve as a form of Internet Passport. Without it, we would not be allowed to do things online.
This kind of system already exists in China, as providing one’s national identification is a requirement for almost all online forums and services.
As such, everything we write, or say, or do online could be monitored, censored, prohibited, leaving us with strict constraints and behavioral controls.
Posting so-called mis/disinformation – whatever the Ministry of Truth says it is – could prove punishing.
Furthermore, the ability to perform financial transactions online could also easily be verboten.
Such restrictions would not be limited to online activities, but could also spillover to other areas such as international travel, shopping, climate lockdowns, woke agenda compliance, and access to services – including government services. They could require the use of Digital IDs for participating in all of these activities.
This will all be done in the name of “cyber security,” for the “greater good,” and to help protect infrastructures against more cyberattacks.
We can easily see where this could all lead, should we submit like sheep and let our spineless sellout politicians get away with such follies (I am not saying that all of them are corrupt, but sadly many are as we have witnessed in recent years, particularly during Covid-19).
Let’s not.
Should this scenario unfold, we must collectively act in unison to ensure that we do not lose an ounce of freedom or rights.
8. How You Can Prepare for the Upcoming Cyber Attack & How to Resist the Upcoming Changes
Preparing for the kind of scenario described in this series, and more specifically outlined in Section 3 above, would be quite similar to what ‘preppers’ do.
For those unfamiliar, preppers are individuals who prepare for the eventuality of either some kind of large natural disaster, or a major financial crisis which would halt essential services and systems, with access to food and water being a primary concern.
There are a lot of prepper websites such as Survive Doomsday, The Organic Prepper, and YouTube channels like the Alaska Prepper. It’s hard to say which is the best; but, the idea is to have a look at them in order to get some ideas of how you can prepare for various contingencies.
These channels and websites also teach their users how to become more self-reliant such as with growing their own food, learning how to filter water, and creating like-minded communities of people who can help – and trust – each other should a crisis hit close to home.
I will simply outline some measures which I think could be useful should a large-scale cyberattack occur, assuming that the electricity grid would also be struck and no longer in service.
Preppers will often make plans to determine a certain length of time they think they need to prepare for. It can be for just a few weeks, or for months.
In the scenario I describe and anticipate, I believe it can easily last for an entire week. Preparing for longer, of course, increases you and your family’s ability to function at least semi-normally during the storm, so to speak.
Some Basic Prepping (for families and individuals)
Three of the most important considerations are: food, water, and cash.
During an outage, cash machines (ATMs) will not be accessible. Having cash at home will enable you to buy for essential goods during this period. As was seen in the Rogers outage in Canada described earlier, people had no cash to take a taxi or pay for other things.
Moreover, your cash is not entirely safe in the bank. As a depositor, you are an unsecured creditor which means that your money is not technically yours; it belongs to the bank. You only have a claim on it. Yes, that’s in the fine print which nobody reads. As such, your funds could be subject to appropriation through legal bail-ins which were described earlier in this post.
Another good idea is to use some of your cash to buy gold or silver coins. During crises, these serve as real money and almost any person or business will accept them. They can be used for barter (exchange of goods/services). The time to buy gold or silver coins is before a crisis hits. Prices of both gold and silver have been suppressed by the banking cartel for the last couple of decades (so that they can maintain the illusion that currencies are not depreciating). That is good news actually; for, it means you can buy these precious metals for relatively cheap prices.
There are many good dealers out there with some popular ones being Kitco and SD Bullion.
It’s also worth considering purchasing some Bitcoin. Though this cryptocurrency is volatile and would not work during a power outage, its monetary network will likely resume once the electrical grid and basic internet are back up. The network is untouchable by governments and the banking cabal (who despise it), for it is impossible for them to seize people’s Bitcoin. If you can’t easily access your money in the bank or transact the usual ways through bank transfers and the like, you could still transact in a peer-to-peer fashion with others who have Bitcoin. This could be used as a good alternative form of money and barter. Furthermore, Bitcoin has a fixed supply of 21 million coins which means it will not depreciate over the long term like traditional (national) fiat currencies.
Regarding food and water, you need to make some estimates as to what you and your family will need to survive for the designated period in which supermarkets may be closed. Non-perishable items such as canned food, dried meat, nuts, drinks, and will be much appreciated should those supermarkets remain closed.
Keep in mind that your city’s or town’s water supply could get cut off if they rely on electricity to run pumps and the like. So, buying plenty of bottled water is a good idea. Moreover, buying some water filtration system or purifying pellets are other ways to help sure you have an adequate supply of clean drinkable water. Boiling water is another alternative, but your will need a source of energy such as a propane stove or the like.
You should always keep at least a month’s worth of supplies such as toilet paper, shampoo, toothpaste, and other bathroom necessities, diapers (if you have children), soap (also to wash dishes and clothes), and the like.
Basic medicine and prescription drugs also need to be considered. Having a first-aid kit, some disinfectant, aspirin, antibiotics, and things of the sort is a good idea; for, during an outage they may be more difficult to obtain.
Energy may also be vital, especially if the outage occurs during winter months or in the dead heat of summer. Though they tend to be a bit costly, gas-powered generators can help power some of your small appliances such as small indoor heaters. Simple things like candles and solar-powered flashlights can also come in handy.
Communications, Community, & Protection
Should landline and cell phone service become unavailable, how will you communicate with friends and family? You can consider simple items such as long-range walkie talkies or satellite phones. Certain satellite phone services may also provide internet connectivity.
Having a good radio could be useful, for it may be one of the only means to receive news and emergency broadcasts.
How well do you know your neighbours? Have they done any prepping? Are there resources you can exchange with them? Have you ever discussed such possibilities with them? It’s probably not a bad idea to get to know them better and plan ahead.
Churches or other places of worship and community centers can also serve as valuable resources during crises. Find out which ones are close by and get to know the people who frequent them.
You should also consider having some weapons or means of protecting your property, goods, and family should an outage become prolonged and get nasty. There’s that old phrase “There are only nine meals between mankind and anarchy,” which serves as a reminder that human beings can become pretty desperate when they and their family members go hungry. As we saw during the Covid-19 crisis, people emptied store shelves pretty quickly, leaving little food to go about. You may also consider helping your neighbours out during a crisis by sharing some food and supplies with them. That is why it is important to get to know them first.
Transportation
During an outage, gas stations may be shut down. It could be a good idea to buy a few portable gas tanks and get them filled up. This way, you’ll be able to continue using your car.
You should also consider owning other vehicles such as gas-powered (not electric) mopeds/scooters or small motorcycles, and even regular bicycles. Such means of transportation to go see your family, friends, and fetch more supplies can come in real handy.
The above are just some of the more pressing things you need to consider. Consult the prepping website for more ideas.
For Business Owners
For small business owners, you may want to consider at least having some kind of backup plan which details how you can run your operations non-digitally.
Can you pay your suppliers by other than electronic means? Can your customers pay you using cash or similar means? How will you pay your employees? Do you have cash on hand to do so?
How will you get critical or important supplies you need? Do you have a reserve inventory of certain goods that may be difficult to obtain during supply chain disruptions?
9. Summary & Conclusion for Part 2
As this has already been a very long post (and series), I will keep this part short.
In summary, we are inevitably coming to an end of an era in twofold fashion: a cyclical or societal one, and a financial/monetary one.
Both of these will consist of radically disruptive shits in the way we live our lives, and how we respond move forward.
When may such a cyberattack occur?
As for a possible date for this global cyberattack, it is hard to say when it would occur. I presume it would happen any time from now until the Fall of 2024, just before the U.S. Presidential Election. It think it would be more likely to occur in winter as opposed to summer since the powers-that-ought-not-be, as evil as they are, would surely like to inflict as much pain and suffering as possible. If you were to press me for a precise date, I would presage either on March 21, 2024 or October 22, 2024.
Human beings have always been quite smart and resourceful in their innate ability to adapt.
This time is no different.
Despite the level of evil present in our world – especially from those who wish to control and enslave us, we each have the divine spark that our Creator has endowed us with, along with freewill and a sublime mind to reason.
Charlie Chaplin magnificently described this innate quality of the human spirit in his famous final speech from the 1940 film The Great Dictator.
The power will return to the people!
What is key in getting through such kind of crisis as described in this series is to remain peaceful, loving, and united – as we saw with great Canadians during the 2022 Trucker’s Convoy.
Be strong. Be brave. Be prepared.
10. Addenda
I have been adding various addenda about some small-scale incidents which have occured since first making this post. Almost all of them appear to be false-flag incidents, given the explanations I have provided.
Also, here is a from an interview I had with investigative journalist Johnny Vedmore in September of last year on this potential large-scale cyber attack, including my take on the Rogers outage:
Addendum #1: 2023-12-02 - Iran:
It should be noted that, likely due to the current uptick in the Israel-Palestine conflict, so-called bad cyber actors such as Iran are seemingly being positioned and prepped to be blamed for the upcoming large-scale (false-flag) cyber attack.
Here is but one instance of how I think they are setting the stage or laying the groundwork to cast blame on the boogeyman that is Iran:
ZeroHedge - Iranian-Backed Hackers Breach Pennsylvania Water Control Station, Display Anti-Israel Messages;
Breitbart - Iran-Backed Hackers Take Control of Pennsylvania Water Station;
CBS News KDKA - Municipal Water Authority of Aliquippa hacked by Iranian-backed cyber group;
Security Week - ICS/OT - Hackers Hijack Industrial Control System at US Water Utility;
The CBS News report stated the following:
Matthew Mottes, the chairman of the board of directors for the Municipal Water Authority of Aliquippa, confirmed to KDKA-TV that the cyber group, known as Cyber Av3ngers, took control of one of the stations. An alarm went off as soon as the hack had occurred.
They also published the following related image, purporting to reveal the signature of the alleged hacker group responsible for the cyber attack on the water plant:
Note that I have contacted the Municipal Water Authority of Aliquippa for confirmation as to whether their chairman Matthew Mottes had indeed confirmed the incident and whether they provided the image (shown above) to them:
Subject: Media Inquiry from journalist in Canada
Hello,
I'm a journalist in Canada (member of the Canadian Association of Journalists / New Canadian Media).
Can you confirm that your Chairman, Matthew Mottes, had told somebody at KDKA-TV news that one of your water stations had "took control" of or was hacked by a group known as CyberAv3ngers?
Also, would it have been Mr. Mottes who sent KDKA-TV or other media the picture of a computer monitor (with Unitronics name displayed at the top) displaying "You have been hacked..."?
If possible, could you send me this picture?
I thank you in advance for your kind and prompt reply.
Sincerely,
Dan Fournier
Associate member of the Canadian Association of Journalists (CAJ) & New Canadian Media (NCM)
I have yet to receive a reply, but will update this section if I do.
I don’t know about you, but this stinks like a rotten fish to me. A setup. Of course this is difficult to prove, but a lot of it doesn’t make a whole lot of sense.
Firstly, they claim that the group responsible is an Iranian hacktivist group called Cyber Aveng3rs who has also purportedly attacked other water plants in Israel who use the same automation software from an Israeli firm called Unitronics.
A prior “attack” on an Israeli facility has been proven false and confirmed as such by another cybersecurity company (Kaspersky).
In addition, the articles reporting on this alleged incident seem to unhesitatingly and promptly confirm (without any evidence provided other than a questionable image) that the hacktivist group is “Iranian-linked.” That is a little absurd in and of itself since any hacker group can have a level of deception and put traces, markers, or signatures that assigns another party. The U.S. has been caught doing this and blaming Russian hackers on the past (see the CIA’s UMBRAGE group section of this post above). So, who is to say this hasn’t happened in this case?
It just seems to me that Iran is the easy villain to employ in order to justify retaliations (from Israel and the U.S.) on the Middle-Eastern nation that just so happens to be Israel’s biggest threat and its most formidable opponent.
I am also contacting BeaverCountian.com who seems to be the first to have reported on the story and has additional photographs from Aliquippa in order to confirm that the photos were sent to them by the water plant.
Addendum #2: 2024-01-09 - The Great Taking:
In Part 1 of this series I outlined how we are coming to and end of the current global monetary system and how a major [fabricated] crisis is needed to put an end to it so that the new, more digital-based, system can emerge whereby the cabal will be able to plunder even more from the masses.
This morning, I came across an outstanding resource that meticulously outlines in great detail how they are going to accomplish this great plundering.
The resource is a book (PDF here) and documentary film called The Great Taking by David Webb that was released late last year and is completely free and accessible to all.
I strongly recommend you at least watch the video to gain an understanding about how our financial world - including banks, financial institutions such as brokers, insurance companies, and the like - have all been compromised by laws that will ensure that the elite at the top of the cabal will have legal dibs on their assets in the event of a systemic financial crash and bankruptcies.
I would recommend downloading a hard copy of the book’s PDF and also the video.
I would also strongly recommend that you share this resources with as many people as you can.
This “Great Taking” has been decades in the making and is likely coming this year or in the next.
Prepare accordingly!
Addendum #3: 2024-03-11 - Russia:
As I had noted in the Comments section for this post, March 11, 2024 could have been a target date for such kind of large-scale cyber attack.
Though a large one did not take place on this day, it has been reported that two cyber attacks have [allegedly] taken place, as per the following report via ZeroHedge:
France & Estonia State Agencies Hit By 'Intense' Cyberattacks, March 12, 2024
Of course, without a full analysis of the “attack” being conducted, the affected parties have pinned the blame on the Russia boogeyman.
Looking through the reports for this so-called cyber attack, we can already see many holes which tend to indicate that they were likely fabricated, false flag type operations.
Here are some examples of such dubious claims about the stated culprit:
"We’ve been seeing over the past few months aggressivity towards European countries through cyberattacks, through disinformation, misinformation campaigns," Barrot said of the Kremlin in a Friday interview with state-run France24.
The passage from above is with regards to the claimed attack on France. Notice how the French Minister Delegate for Europe, Jean-Noël Barrot, equates disinformation and misinformation as actual cyberattacks. This is a ridiculous claim in and of itself, for pretty much any information posted online and on social media could be considered as such and tantamount to a cyber attack. Abolute ridiculous nonsense.
Next, regarding the alleged cyber attack on Estonia, the ZeroHedge article references how regional media pointed to pro-Kremlin hackers for a devastating DDoS attack.
The news media outlet they link to is that of TVP World (a Polish international news network) with the article titled Estonian gov’t institutions targeted in largest cyber attack in country’s history (dated March 11, 2024):
Firstly, notice the choice of cover image they have chosen for this piece; it stinks of propaganda.
Next, the piece states that the attack was “claimed by pro-Kremlin hackers,” as reported by the Postimees newspaper on Monday. They do not link to the article by Postimees newspaper, nor to they provide any links to any such claim by the so-called pro-Kremlin hackers. Zero evidence. Pure hearsay (unsubstantiated information).
They reference officials from Estonian Information Systems Authority (RIA) and cite from their “spokespersons” (which is odd since usually there is only one spokesperson)":
“Pro-Kremlin hacker groups have been primarily claiming responsibility for the attacks, as was the case last weekend,” noted the Estonian agency.
Notice the word ‘primarily’ which I have purposely bolded. Here, primarily appears to imply partially. Hackers usually either claim full responsibility or not at all.
More to the point, the Postimees newspaper article they cite from uses similar misleading language, stating:
«Pro-Kremlin hacktivist groups have mostly claimed responsibility for the attacks, and this was also the case last weekend,» the spokespeople said.
Here, the Polish news outlet Postimees use the term ‘mostly’ (which I have also bolded). What is that even supposed to mean “mostly”? Again, this implies that a supposed hacker group has claimed partial responsibility which, once again, is highly unlikely and makes little sense.
Moreover, they provide zero evidence of this allegation. No sources. No links. Nothing.
As with previous alleged cyber attacks (see previous addendums in this post) these two on France and Estonia just stink of false flag operations in which media outlets purposely put out pieces with next to no evidence to substantiate claims of attacks and their culprits. They merely cite from agency officials some talking points without even bothering on checking the veracity of those statements. Journalism at its best, no?
I expect to see a whole bunch more of these so-called cyber attacks in the coming months in order to continue to construct this [false] narrative and propagate it in the minds of their viewers to set the stage for a, likely, large-scale false flag.
I will continue to document them with more addendums in this post going forward.
Stay tuned.
Addendum #4: 2024-04-20 - China:
Here we go again folks. More ground work is being layed for a false flag to be blamed on the boogeyman, China.
ZeroHedge: FBI Warns Of Risk Of Chinese Hack Attack On Energy Infrastructure, April 19, 2024 (alternate link via Oilprice.com)
The article cites comments made by FBI Director Christopher Wray who spoke at the Vanderbilt Summit on Modern Conflict and Emerging Threats (April 17-18, 2024).
From the article:
Speaking at the Vanderbilt Summit on Modern Conflict and Emerging Threats, Christopher Wray said:
“The PRC [People’s Republic of China] has made it clear that it considers every sector that makes our society run as fair game in its bid to dominate on the world stage, and that its plan is to land low blows against civilian infrastructure to try to induce panic and break America’s will to resist.”
This is a quote from FBI Director, Christopher Wray. Saying that China has “made it clear” that it has a bid to “dominate the world” is an absolutely absurd statement.
Anyone who knows history (and I have studied Chinese history in depth, also having lived 13 years in the Middle Kingdom), can pretty much see that China has not invaded, colonised, or dominated other regions like the United States has (with the exception of Tibet, and parts of the South China Sea). So, such a statement is more projection than anything else (but propaganda can be considered a close second).
Furthermore Wray states that China has a plan to “land blows against civilian [American] infrastructure,” yet provides very little evidence to support this statement. He only provides hearsay and, at best, very weak circumstantial evidence.
Even in the April 18, 2024 FBI News report Chinese Government Poses 'Bold and Unrelenting' Threat to U.S. Critical Infrastructure, FBI Director Says Wray further emphasises the alleged threat:
“The fact is, the PRC’s targeting of our critical infrastructure is both broad and unrelenting,” he said. And, he added, the immense size—and expanding nature—of the CCP’s hacking program isn’t just aimed at stealing American intellectual property. “It’s using that mass, those numbers, to give itself the ability to physically wreak havoc on our critical infrastructure at a time of its choosing,”
Language is everything. In this FBI article, the only “evidence” (which is more hearsay than evidence) Wray offers is:
This risk isn’t new, he said. CCP-sponsored cyber actors "prepositioned” themselves to potentially mount cyber offenses against American energy companies in 2011—targeting 23 different pipeline operators.
Notice that I have bolded the word potentially. It is not stated that China committed the offense, but rather that it “prepositioned” to potentially mount a cyber offense. That’s a HUGE difference.
This is a common tactic (like I’ve shown before) that these intelligence agencies use to trick and deceive the press to make it sound like actual offenses have indeed taken place when no proof actually exists or has been presented to show that they have taken place.
Wray does, however, make some valid points about the CCP (Chinese Communist Party)’s cyber and espionage capabilities. The CCP does indeed have an extensive track record of stealing IP (Intellectual Property).
But the apparent reason for stating this here, at least from my assessment, is to conflate the two. In other words, it is used to vilify the CCP and thus provide a tarnishing effect on its reputation.
The FBI article provides ZERO links to actual (verifiable) evidence it purports to have regarding the CCP’s cyber activities.
Does the CCP have extensive cyber capabilities? Absolutely, perhaps tops in the world along with the U.S. and Russia.
But that doesn’t necessarily mean that they are intent on doing so, i.e., on using these cyber capabilities to “wreak havoc on our critical infrastructure at a time of its choosing.” That is merely speculation on the part of Wray.
Could there be some merit to it though? Yes, perhaps. But if Wray is to be credible, he needs to provide the receipts, i.e., tangible evidence of such kinds of cyber hacks on U.S. critical infrastructure; and for this, Wray does not.
Also from the FBI article:
“It’s using that mass, those numbers, to give itself the ability to physically wreak havoc on our critical infrastructure at a time of its choosing,” he said.
Notice Wray’s words - “wreak havoc on our critical infrastructure at a time of its choosing.” Again, this is speculatory language. “At a time of its choosing,” implies an imminent danger. This is to create fear and angst. A common tactic used in the military. It is not based on sound intelligence - I say this because he DOES NOT provide sound intelligence (i.e., specific reports or documents) that support these supposed threats.
Unlike FBI Director Christopher Wray, I am willing label my own comments that are speculation: I believe that the FBI is being deceitful in this reporting (especially since they are not forthcoming with evidence) with the intent of further tarnishing the reputation of China and instilling the doubt in the press’ and the general public mind that the Asian boogeyman is a big bad threat and are about to attack Western infrstructure at any minute.
Question everything!
Addendum #5: 2024-05-27 - China again:
Yet again with the Big Bad Red Dragon folks.
This time, the hype was reported by ZeroHedge: US-UK Intelligence Warning: China Cyberthreats Pose 'Epoch-Defining' Challenge (May 23, 2024).
It’s pretty much the same playbook. So, I’ll keep it brief and give you some of the main highlights.
Here’s some propaganda by none other than Reuters in the linked article Britain and US sound alarm over growing Chinese cyber threat.
Of course, we have the usual deceptive use of words such as “could,” “may,” “likely,” and the like. Nothing real, mostly speculation.
The article also states [emphasis added]:
Prime Minister Rishi Sunak said on Monday Britain faced a threat from "an axis of authoritarian states like Russia, Iran, North Korea, and China",
“Like” China or Russia or Iran, doesn’t mean it is them.
This is language used to suggest they are guilty without, of course, providing any verifiable evidence.
Yet another linked article from Reuters, this time US confronts China over Volt Typhoon cyber espionage employs the same deceptive tactic.
And this time they use a catchy moniker like “Volt Typhoon” to make it stick more and make the fiction sound more dangerous.
Similar verbiage / speculatory language without presenting any evidence.
And yet another Reuters article What is Volt Typhoon, the Chinese hacking group the FBI warns could deal a 'devastating blow'? employs the same garbage [emphasis added]:
April 19 (Reuters) - China is developing the "ability to physically wreak havoc" on U.S. critical infrastructure and its hackers are waiting "for just the right moment to deal a devastating blow", FBI Director Christopher Wray said on Thursday.
And more [emphasis added]:
TAIWAN BOTNET
Does this mean a group of destructive hackers is preparing to sabotage U.S. infrastructure in the event of a conflict over Taiwan?
Microsoft qualified its assessment last year as "moderate confidence," intelligence jargon that typically means a theory is plausible and credibly sourced but has yet to be fully corroborated. Different researchers have identified various aspects of the group.
This time, it is with the so-called threat level which is basically something they pull out of their asses. “Moderate confidence” means Jack shit. These are empty presumptions that hold practically no merit.
It’s all verbiage and false notions to be implanted in the readers’ minds to make it seem like China (or whatever targeted group) are already guilty of wrongdoing.
Rinse and Repeat.
Expect more of this nonsense in the coming months which I’ll be keeping track of and posting here.
Addendum #6: 2024-06-14 - China again, Third time’s a charm (The Epoch Times)
Yet again.
This time it is The Epoch Times.
To me, this is dissapointing but not surprising. I hold The Epoch Times in high regard for its reporting (espcially of its coverage for Canada and the U.S.) and am even a monthly subscriber. I know that this news outlet, owned by Epoch Media Group, was founded by former Chinese dissidents. Thus, most of their reporting on China must be taken with a grain of salt, given inevitable bias and anti-China sentiment which stems from the top of the media organisation.
That being said, let’s have a look at this particular article (and a few it links to).
The June 12, 2024 article titled China-Linked Cyber Campaign Infiltrated Dozens of Western Governments: Dutch Intelligence (archived here) stinks of the usual problems as those listed in previous addenda (above in this post).
For instance, the use of suggestive language is present [with emphasis added]:
The scope of the latest discovery suggests that the campaign sought to gain persistent access to the defense industries of Western nations.
This is a news article, not an opinion piece. The author, Andrew Thornebrooke, is merely suggesting that the China-linked cyber campaign “sought to gain persistent access to the defense industries of Western nations.”
That statement is problematic in many ways. First, by using the word suggest the author is making a presumption.
Secondly, this is his opinion that is not backed by any evidence or accompanying statement by authorities.
More speculative language hereunder [with emphasis added]:
Because zero-day vulnerabilities are hard to anticipate, the statement said, the government encouraged the adoption of an “assume breach” principle. This means that an initial breach should be assumed and efforts should be taken to limit the damage.
Though the author is citing a government source, Thornebrooke re-amplifies the speculatory nature of the statement by stating that a [hacker] breach “should be assumed.”
Instead of doing his job as a journalist and questioning the government official for proof on the matter, he just spews their statements which are to be taken as gospel.
This is poor reporting.
Thornebrooke’s piece also links to two other of his own articles which use the same kind of speculatory language and which lack substantial or even believable proof or evidence.
What is interesting about Thornebrooke are his choices for cover images.
Here are the images he used for his two articles:
For added clarity, here are the respective texts of the captions:
Caption 1:
"Prince," a member of the hacking group Red Hacker Alliance who declined to give his real name, uses a website that monitors global cyberattacks on his computer at their office in Dongguan, Guangdong Province, China, on Aug. 4, 2020. (Nicolas Asfouri/AFP via Getty Images)
Caption 2:
A hacker uses his computer in Dongguan, China's southern Guangdong Province, on Aug. 4, 2020. (Nicolas Asfouri/AFP via Getty Images)
There are so many red flags with these, I’m not sure where to start.
The source for both photographs are from AFP (Agence France-Presse) photographer Nicolas Asfouri.
The first caption states that “Prince” is a member of a hacking group called Red Hacker Alliance. According to DBPedia, the last activity by this group goes back to 2008. The photograph is said to have been taken on August 4, 2020. Almost no other information about this alleged hacker group seems available on the internet. So proof of their current existence is quite scarce, to say the least.
How realistic do you think it is for a photojournalist to have gained access to the premises of a hacker group in China?
I lived and worked in China for 13 and one thing I know for sure if that security is extremely tight everywhere you go. If this were some kind of state-sponsored hacker unit, there is no way in hell a foreigner - especially a photojournalist - would gain access to such a location. Impossible.
If it was an informal hacking group, it remains to be contemplated on how Mr. Asfouri could have 1) made contact with such a Chinese hacker, and 2) gain access to their operating area. Is it possible? Maybe, but extremely unlikely. Why? Because most citizens in China fear their government and are very well aware that they are being constantly watched. So, for any hacker to put him/herself in a compromising position by letting a photojournalist take photos of their actions would surely invite a visit by CCP thugs and they’d risk being thrown into a dark prison. They would not be foolish enough to risk it.
In addition, look at the graphics of the two photographs. The left hand of the hacker is in exactly the same position in both photographs. How likely is that given that the contents of the screens are different (which suggests the shots would have been taken at least one second or more apart)?
I tried to contact the photojournalist Nicolas Asfouri with questions and a request for comment (see my text below), but the form on his contact page renders errors and the message could not be forwarded.
I have sent an email to AFP to try to obtain his email address so that I can make my media inquiry to him. Should I be able to reach Mr. Asfouri by email followed by a reply on his part, I will be sure to add it to this addendum.
Here was the email I wanted to send to photojournalist Nicolas Asfouri:
Subject: Media inquiry about a Chinese hacker photo attributed to you
Text: Dear Mr. Asfouri,
I'm an independent journalist in Canada. I have come across a photo from an article in The Epoch times (see https://www.theepochtimes.com/china/china-linked-cyber-campaign-infiltrated-dozens-of-western-governments-report-5667428) whose caption has your name with AFP.
a) Can you confirm this is your photograph?
b) The caption reads: "Prince," a member of the hacking group Red Hacker Alliance who declined to give his real name, uses a website that monitors global cyberattacks on his computer at their office in Dongguan, Guangdong Province, China, on Aug. 4, 2020." - So, can you confirm that you took this photograph yourself in front of this hacker, or how you obtained it?
c) There's another photograph that is almost identical to the previous one (but with a variation - a globe on the second computer screen of the hacker). Did you take this photograph too? Was it, for instance, taken perhaps a few seconds or minutes before or after the other photograph previously mentioned?
I thank you in advance for your clarifications on these photographs.
Sincerely,
So once again, we have dubious articles about alleged Chinese cyber threats that use vague and speculatory language, and provide next to no tangible evidence or proof that a Chinese group comitted the so-called hack.
I have also made a media inquiry to The Epoch Times concerning the poor quality of Mr. Thornebrooke reporting and will post their reply should it be forthcoming.
Update: As of 2024-08-12 I have yet to receive a reply from The Epoch Times.
Addendum #7: 2024-08-12 - Iran - Trump Campaign “Hack”:
This time, the boogeyman du jour is Iran and it has all the usual hallmarks of a false flag.
And, once again, it is being reported on by The Epoch Times (alternate link via ZeroHedge):
Microsoft Says US Presidential Campaign Targeted by Iran-Backed Hackers; Trump Campaign Confirms Breach, 8/10/2024
And also once again, we have Bill Gates’ Microsoft contributing what can only be considered as lies to the fairy tale hack.
And what would a good false flag be without a catchy name for the operation to help “legitimise” it? In this case since we are dealing with Iran, why not call it “Mint Sandstorm”? As per the article [with original link included']:
The report from the Microsoft Threat Analysis Center (MTAC) indicates that an Iranian group called Mint Sandstorm that is connected to the Islamic Revolutionary Guard Corps sent a spear phishing email in June to a high-ranking official on a presidential campaign from the compromised email account belonging to a former senior campaign adviser.
The August 9, 2024 Microsoft Threat Analysis Center (MTAC) report titled ‘Iran steps into US election 2024 with cyber-enabled influence operations’ (archived here) wreaks of fabricated information.
For instance, the report employs the usual speculatory verbiage which does not firmly confirm their supposed findings:
Recent activity suggests the Iranian regime—along with the Kremlin—may be equally engaged in election 2024.
Notice from the passage from the report above uses two such speculatory terms: “suggests” and “may be.” This is very typical in these types of reports (as showcased in other addenda above in this post), for it is a technique to make it appear as though it is legitemately confirmed while, in actuality, it is not.
Moreover, they do not provide evidence or specific reports regarding these “activities,” as is typically the case with the others (see previous addenda).
Here’s another excerpt/example from the MTAC’s report:
Iranian actors have recently laid the groundwork for influence operations aimed at US audiences and potentially seeking to impact the 2024 US presidential election. This recent cyber-enabled influence activity arises from a combination of actors which are conducting initial cyber reconnaissance and seeding online personas and websites into the information space.
Notice the word “potentially” in the first sentence;l again, pure speculation. Could such “influence operations” being actually occurring? Of course. But, the fact that they do not provide a scintilla of evidence removes the credibility of their so-called assertions. They imply that the Iranians are “seeding online personas and websites” into the information space. Okay, that is totally plausible. But why don’t they provide a single example of one such online personas (assumming they mean influencer(s)) or even one website? Probably because it is TOTAL BS.
An what would a cyber threat assessment be without a fancy graphic to further “legitimise”?
But again, ZERO evidence or links to these purported operations at the behest of the Iranian regime. But hey, the graphic looks very nice and professional, seemingly totally legit, right?
The Epoch Times article states Steven Cheung, a spokesperson for the Trump campaign, confirmed the breach as was told to Politico. What is notable is that Cheung expressed that the hack was attributed to “foreign sources hostile to the United States.” No specifics as to who exactly these foreign sources are, exactly.
Moreover, Politico stated that it began receiving its emails (about the purported hack) from an anonymous source using the alias “Robert.” How convenient! This is once again so typical of this type of false flag set up. As an anonymous source cannot be vetted, we are simply supposed to gobble it all up and take their word for it. Again, I call BS on this - and it certainly isn’t the first time that Politico has engaged in this kind of complicit behaviour, or propaganda.
Finally, the Epoch Times article references a Office of the Director of National Intelligence (ODNI) statement that is very broadly worded (speculatory) and offers next to nothing in terms of verifiable evidence to support their claims.
Is election interference occurring by Russia, China, and Iran? No doubt it is, just like the U.S. does with its own Interactive Internet Activities (IIAs) operations. But to just bundle up a bunch of assertions without tangible evidence about yet another purported hack (in this case the Trump campaign) stinks of yet another set up or form of predictive programming to prepare the masses for the big false flag they indend to thrust upon us, likely this Fall.
Addendum #8: 2024-09-20 - Iran - Trump Campaign “Hack” take two!
Here we go again folks.
Same playbook. Similar actors. New pundits.
Let’s decipher this one.
First the headlines:
ZeroHedge - FBI Reveals That Iran Hacked Trump Campaign Materials And Handed To Biden/Harris. Sep 19, 2024
POLITICO - We received internal Trump documents from ‘Robert.’ Then the campaign confirmed it was hacked. 08/10/2024
AP’s Meg Kinnard’s Sept. 18, 2024 X post: “WASHINGTON (AP) — FBI: Iranian hackers sent unsolicited information stolen from Trump campaign to people associated with Biden's campaign.”
AP - Iranian hackers tried but failed to interest Biden’s campaign in stolen Trump info, FBI says, September 18, 2024
Okay, so let’s start with the first one citing the FBI. I think at this point, it is pretty safe to assume that the FBI is not an institution that can be trusted, especially given that they destroyed evidence of the Trump assassination attempt in Butler, Pennsylvanie the day after the incident.
I’d rather focus on the POLITICO article, for it showcases the usual deceptive tricks (as detailed in the previous addenda to this post).
So, let’s dissect it a bit…
Here are the first three paragraphs of the POLITICO article:
Former President Donald Trump’s campaign said Saturday that some of its internal communications had been hacked.
The acknowledgment came after POLITICO began receiving emails from an anonymous account with documents from inside Trump’s operation.
The campaign blamed “foreign sources hostile to the United States,” citing a Microsoft report on Friday that Iranian hackers “sent a spear phishing email in June to a high-ranking official on a presidential campaign.” Microsoft did not identify the campaign targeted by the email and declined to comment Saturday. POLITICO has not independently verified the identity of the hacker or their motivation, and a Trump campaign spokesperson, Steven Cheung, declined to say if they had further information substantiating the campaign’s suggestion that it was targeted by Iran.
POLITICO states that it had received “emails from an anonymous account with documents from inside Trump’s operation.” Two red flags righ from the start here, folks. Isn’t it always from an anonymous source? That way, it cannot be verified. How convenient. Next, even though they state they received documents from the Trump campaign, no such documents nor their specific contents has been revealed by POLITICO. Why? If they had such incriminating documents, then why not publish them? Sure, there could be some sensitive information in it, but such parts could easily be redacted as is the common practice in journalism. Yet, POLITICO didn’t do so and, as such, they wreak of insincerity.
In the third paragraph cited above, they refer to an older Microsoft report (dated August 8, 2024) stating a phishing scam. This is deceptive reporting, as it conveys or implies that this report has to do with the current “hack,” which it doesn’t. Also, just have a look at the “Iran boogeyman” image Microsoft used for that “report”:
In that same paragraph, POLITICO stated that Microsoft “did not identify the campaign targeted” and that they “declined to comment.” Really? So, in other words the Microsoft claim has zero substance if they cannot back up their allegations.
Again in the same paragraph it is stated that “Trump campaign spokesperson, Steven Cheung, declined to say if they had further information substantiating the campaign’s suggestion that it was targeted by Iran.” Notice the vague word “suggestion” when irresponsibly stating that Iran was involved. No proof at all, just speculation!
The fourth paragraph from the POLITICO fiction piece reads as follows:
“These documents were obtained illegally from foreign sources hostile to the United States, intended to interfere with the 2024 election and sow chaos throughout our Democratic process,” Cheung said. “On Friday, a new report from Microsoft found that Iranian hackers broke into the account of a ‘high ranking official’ on the U.S. presidential campaign in June 2024, which coincides with the close timing of President Trump’s selection of a vice presidential nominee.”
Firstly, they refer to another alleged hack from June 2024.
Moreover, POLITICO cites a “new report” from Microsoft; though they do not link to it, the only one available on Microsoft’s site is one dated September 18, 2024 which must be the one they are referring to. This one is titled Securing US Elections from Nation-State Adversaries. I have looked through this piece and in it, nothing indicates a specific recent hack on the Trump campaign; rather, it just warms over old Iran claims. Nothing. Zero. Nada. Zip.
So, it’s easy to see that there is no actual documentation about this alleged second “hack” on the Trump campaign.
Furthermore, in the third paragraph above, it says “POLITICO has not independently verified the identity of the hacker or their motivation, and a Trump campaign spokesperson, Steven Cheung, declined to say if they had further information substantiating the campaign’s suggestion that it was targeted by Iran.”
Trump’s spokesperson Steven Cheung declined to comment with substantiating information about the Iran hack claim? Really? This just adds to the fishiness of this whole charade.
So, again, this so-called hack appears to be nothing more than speculation.
In fact, I would dare to say that the piece is either a complete fabrication, propaganda, predictive programming, or all of the above, take your pick!
By predictive programming I mean the following:
“foreign sources hostile to the United States, intended to interfere with the 2024 election and sow chaos throughout our Democratic process”
It’s almost as if they are instilling the through in the American mindset that “chaos” may ensue due to this “interference.”
How can POLITICO hold any credibility whatsoever with such kind of “reporting”?
Then, there’s the AP report by Meg Kinnard - which comes in the unusual form of a X post. There is, however, an September 18 AP article titled ‘Iranian hackers tried but failed to interest Biden’s campaign in stolen Trump info, FBI says,’ but it is pretty much without any substance or corroborating evidence. The only claim - if you can even call it that - is the following [with emphasis added]
In a statement, Harris campaign spokesperson Morgan Finkelstein said the campaign has cooperated with law enforcement since learning that people associated with Biden’s team were among the recipients of the emails.
“We’re not aware of any material being sent directly to the campaign; a few individuals were targeted on their personal emails with what looked like a spam or phishing attempt,” Finkelstein said. “We condemn in the strongest terms any effort by foreign actors to interfere in U.S. elections including this unwelcome and unacceptable malicious activity.
So, just a possible “phishing” attempt to the alleged Harris team, but nothing about an actual hack.
I would again argue, how can the AP have credibility with such kind of hollow reporting?
They are really getting sloppy as hell folks. I am glad that I am documenting this all for posterity.
Addendum #9: 2024-11-19 - Back to the Big Red Dragon, China who supposedly hacked T-Mobile (as per “reports” by the Wall Street Journal)
Yes, folks here we go again. And it is the same routine, re-packed - like death warmed over - to keep the Big Red Dragon boogeyman (a.k.a., China) lurking in the shadows.
You see, even while the new Trump Administration seems to be focused on Iran (like I have already covered in previous addenda shown above in this post), the Military-Industrial Complex still in charge of D.C. needs a big boogeyman since Orange Man has promised to end the war between Russia and the Ukraine.
So, please oblige me to let you in on more of these ridiculous shenanigans.
And this time, it is the Wall Street Journal (WSJ) who is spewing this garbage.
I’ll try to keep this one relatively short, but you will see the same old dog-and-poney show tricks at work.
A November 16 piece from the New York Post titled T-Mobile hacked in massive Chinese breach of telecom networks, WSJ reports immediately caught my attention.
Firstly, it must be stated that the NYPost piece has nothing original and is simply serving as a banal regurgitation of previous “reports” from the WSJ. So, I won’t dissect this one, and instead focus on the main article from the WSJ:
WSJ: T-Mobile Hacked in Massive Chinese Breach of Telecom Networks, Nov. 15, 2024
The second paragraph of this article reads as follows:
Hackers linked to a Chinese intelligence agency were able to breach T-Mobile as part of monthslong campaign to spy on the cellphone communications of high-value intelligence targets. It is unclear what information, if any, was taken about T-Mobile customers’ calls and communications records.
The phrase “Hackers linked to a Chinese intelligence agency” is presented without any mention of a specifc group. It is not backed at all. There is one group mentioned in the article called “Salt Typhoon,” but it is not the one that is alleged to have hacked T-Mobile. So, right from the start the needle from the bullshit meter is up and to the far right.
In the same paragraph they state: “It is unclear what information, if any” was taken about T-Mobile customers’ calls. In other words, there is no proof whatsoever that informatioin or communications records were indeed taken/copied/breached.
The third paragraph is also problematic:
“T-Mobile is closely monitoring this industry-wide attack, and at this time, T-Mobile systems and data have not been impacted in any significant way, and we have no evidence of impacts to customer information,” a company spokeswoman said. “We will continue to monitor this closely, working with industry peers and the relevant authorities.”
What is strange about this WSJ report is that T-Mobile itself denies even ever having been hacked!
Quoting from above: “T-Mobile systems and data have not been impacted in any significant way.” The word “impacted” here is important. One could easily surmise that if they had been hacked, that would certainly count as an impact, no?
Furthermore, the sentence continues: “and we have no evidence of impacts to customer information,” T-Mobile’s spokesperson affirmed - which again provides zero evidence of an actual hack.
The following paragraph reads:
The compromise of T-Mobile expands the list of known victims of a cyber-espionage campaign by Chinese hackers—dubbed Salt Typhoon—that some U.S. officials consider to be historic and catastrophic in scope and severity. The Journal previously reported in October that AT&T, Verizon and Lumen Technologies were among the telecom companies that suffered an intrusion.
Here, the article states “some U.S. officials” without naming them at all. Who are these officials? From what specific agency? So, again there is no verifiability for these claims.
More skullduggery in the paragraph that follows:
The group used sophisticated methods to infiltrate American telecom infrastructure through vulnerabilities including Cisco Systems routers, and investigators suspect the hackers relied on artificial intelligence or machine learning to further their espionage operations , people familiar with the matter said. The attackers penetrated at least some of that infrastructure over eight months or more.
This paragraph commences “The group used sophisticated methods…” Which group? Again, they are not being specific. There is no specific name of the alleged hacker or group which makes one wonder if they are just making this [shit] up.
Then we have the very common insert “people familiar with the matter” which is a major red flag because it implies an ANONYMOUS, non-verifiable source.
Hence, while such kinds of statements appear to provide some kind of believability, in reality it is all just heresay that can never be corroborated.
Another paragraph finally provides a source - in this case the FBI and the Cybersecurity and Infrastructure Security Agency (CISA):
Chinese government-linked hackers had compromised networks at multiple telecommunications companies “to enable the theft of customer call records data, the compromise of private communications of a limited number of individuals who are primarily involved in government or political activity, and the copying of certain information that was subject to U.S. law enforcement requests pursuant to court orders,” the statement from the Federal Bureau of Investigation and Cybersecurity and Infrastructure Security Agency said.
Even though they don’t link to this source, it can easily be located by a Google search - which I did. I found an official Joint Statement by the FBI and CISA dated November 13, 2024 to this effect:
Unsurprisingly, this joint statement provides zero verifiable evidence regarding the claim.
In other words, we are just to take their word for it.
Hogwash.
Could China have targeted and hacked or breached said telecommunications? Yes, absolutely. But without any kind of actual evidence presented, it is once again merely heresay.
That’s enough for this first WSJ article.
But, I’d like to very briefly go over a couple of other ones, so as to show that if you repeat a lie often enough, people will more likely be inclined to believe it (whomever actually said this).
Here is the second article that the WSJ links to from the former: U.S. Wiretap Systems Targeted in China-Linked Hack, dated Oct. 5, 2024.
The piece commences:
A cyberattack tied to the Chinese government penetrated the networks of a swath of U.S. broadband providers, potentially accessing information from systems the federal government uses for court-authorized network wiretapping requests.
Keep in mind this is a news article, not an opinion piece. Yet right from the start it is the WSJ authors who are making the bold claim that the Chinese government did a cyber attack without referring to any particular expert source.
Is this reporting or propaganda?
The second paragraph:
For months or longer, the hackers might have held access to network infrastructure used to cooperate with lawful U.S. requests for communications data, according to people familiar with the matter, which amounts to a major national security risk. The attackers also had access to other tranches of more generic internet traffic, they said.
This paragraph employs two usual tricks: 1) vague/speculative language, and 2) an anonymous source.
The hackers “might have” is pure speculation!
And the phrase “according to people familiar with the matter,” also shows anonymity.
Who are these people familiar with the matter? These reporters are either being very sloppy/careless in providing credible sources, or are deliberately using this trick to spew propaganda.
More of the same [bolded]:
It appeared to be geared toward intelligence collection, the people said.
And “the people said,” is not proper English which further shows their sloppiness.
More speculation [bolded]:
The hackers appear to have engaged in a vast collection of internet traffic from internet service providers that count businesses large and small, and millions of Americans, as their customers.
Again [bolded]:
More recently officials have been alarmed by alleged efforts by Chinese intelligence officers to burrow into vulnerable U.S. critical infrastructure networks, such as water-treatment facilities, power stations and airports. They say the efforts appear to be an attempt by hackers to position themselves in such a way that they could activate disruptive cyberattacks in the event of a major conflict with the U.S.
Firstly, “by alleged efforts by Chinese intelligence officers” shows you that these are merely allegations with zero backing.
There’s more, but we’ll leave it at that for that article.
Here’s another one from the WSJ dated October 25, 2024: Chinese Hackers Targeted Phones of Trump, Vance, and Harris Campaign.
An anonymous source from the very first paragraph [bolded]:
WASHINGTON—The Chinese hackers who burrowed into the networks of U.S. telecommunications firms have used their deep access to target the phones of former President Donald Trump, his running mate, JD Vance, and people affiliated with Vice President Kamala Harris’s presidential campaign, according to people familiar with the matter.
The second paragrap shows the usual vague/speculative language [bolded]:
It wasn’t clear what data the hackers were able to obtain from any of these devices. The hackers are believed to be tied to China’s intelligence services.
Can you see how sloppy these same authors are?
I will spare you with more sufferring, as I think you get the picture.
The only thing I would add here is that this type of propaganda is spewed using different mainstream news outlets like The Epoch Times / CBS / NYPost / Reuters / AFP / Politico in order to make it appear more credible while reaching a larger audience.
I was thinking of contacting the reporters from the WSJ since their email addresses appear at the end of their pieces, but then was reminded by a favourite quote from Sun Tzu’s Art of War:
“Never interrupt your enemy when he is making a mistake.”
Addendum #10: 2024-12-06 - Same Shit, Different Day (China again brought to you by The Epoch Times)
Well, this is just a rinse-and-repeat operation.
And since they want to target China, they definitely had to choose The Epoch Times which, as I have mentioned earlier, has obvious biases against China (I know that this news outlet, owned by Epoch Media Group, was founded by former Chinese dissidents. Thus, most of their reporting on China must be taken with a grain of salt, given inevitable bias and anti-China sentiment which stems from the top of the media organisation.)
That being said, here is the hit piece:
China-Linked Hackers Breached 8 US Telecom Companies, White House Says, by Frank Fang, 12/5/2024 (also accessible via ZeroHedge)
I won’t do a total dissection again since, firstly, the article is so empty of any real evidence, and secondly, it’s just the same old deceptive tricks. So, you will be able to recognise them quite quickly.
Also, right off the bat the “top” Whitehouse official Anne Neuberger who is deputy national security adviser for cyber and emerging technologies said:
“We don’t believe any classified communications has been compromised.”
Really? Then why hold a freakin press conference? You just contradicted your whole premise that the Chinese had breached the telecom infrastructure. What an oxymoron!
Usual deceptive tricks:
Vague language used such as: “appeared,” “likely.”
No real evidence presented
Scary hacker group names to make them sound more threatening: “Salt Typhoon,” “Flax Typhoon,” and “Volt Typhoon.” What a joke!
Unstated parties: “Additionally, the official said a “couple dozen” countries have been impacted by the Chinese hacking.” Really? A “couple dozen”? Which [24 or so] countries? You know, that could be relevant information so that we can independently verify whether they can confirm any of your stated allegations.
I’m telling you, they are getting so lame and sloppy, just tarnishing any kind of journalistic integrity they have for their entire publication.
Plus, the Epoch Times anti-China agenda is becoming to obvious to hide.
Gatekeeper media.
Addendum #11: 2024-12-31 - U.S. Treasury alleged hack by China, and again zero evidence provided to verify or confirm it
As per a December 31, 2024 Reuters article titled US Treasury says Chinese hackers stole documents in 'major incident', the U.S. Treasury says Chinese state-sponsored hackers stole documents.
The U.S. Treasury called it a major incident and wrote a letter to two members of the Committee on Banking, Housing and Urban Affairs, namely Sherrod Brown and Tim Scott.
The letter states that the Treasury was notified by a third-party software service provider, BeyondTrust, that “a threat actor had gained access to a key used by the vendor to secure a cloud-based service used to remotely provide technical support for Treasury Departmental Offices (DO) end users.”
The letter later notes: “Based on available indicators, the incident has been attributed to a China state-sponsored Advanced Persistent Threat (APT) actor.”
This is an unsubstantiated statement by Aditi Hardikar (Assistant Secretary for Management U.S. Department of the Treasury) who wrote the letter, as neither BeyondTrust nor CISA nor the FBI appears to have confirmed that China was involved or suspected on their respective official news feeds during the month of December of this year.
So, why would Hardikar state it as a fact without providing any evidence or statements from the three cybersecurity experts?
Who exactly did she get this assertion from?
Was she instructed to write this? If so, by whom?
Once again this stinks to high heaven and appears to be yet another instance to make it seem like critical infrastructure - in this case the U.S. monetary system - is vulnerable to cyberattacks.
One has to wonder whether the current unsustainable level of U.S. Debt (currently sitting at around $36 trillion) has do to with this alleged, likely completely fabricated, cyberattack.
In a recent series, I wrote about how the U.S. Federal Reserve is actually insolvent based on their on data (as reported on by Matthew Kratter):
You can watch Matthew Kratter’s video on the insolvency of the Fed hereunder:
To sum up, it is very well possible that since the U.S. Monetary system is coming to an end, those who have been controlling it for over a century are seeking a way to blow it up (to introduce their new, digital system) - hence the convenience of a huge cyberattack with a culprit such as China, Russia, or Iran. They have enabled this debt mess and certainly don’t want to be blamed for their recklessness.
Stay tuned, 2025 will be interesting to say the least.
Addendum #12: 2025-01-05 - The Epoch Times going All-in Against Big Bad China
Well, no surprise here.
And we find the same “journalist” from The Epoch Times Andrew Thornebrooke spewing on the propaganda nice and thick in his latest piece which I will reference below.
In my previous addendum above (from 2024-06-14), I outlined the ridiculous reporting of this author and had even made a media inquiry to The Epoch Times which, of course, they failed to answer.
Now, he packs it on thick in his latest chef d’oevre titled China's Massive Hacking Campaign Targeting The US (read the article via ZeroHedge).
The article is basically a collage of prior lies and propaganda. I won’t even bother to go over the ridiculous contentions therein, as most of its contents consists of made-up fairy tales.
As I mentioned previously, The Epoch Times was started by former Chinese dissidents who were persecuted by the Chinese Communist Party (CCP) and have published countless pieces with clear bias against China.
Though there has been many pieces that contain truthful and accurate information (as per my first-hand observations of having lived in China between 2008 and 2021), we can easily see when specific articles are merely hit pieces designed to showcase the country in a dark or negative light. And this piece is one of them.
And the timing of this particular piece is somewhat suspicious given the latest rhetoric (read fabricated propaganda) about Chinese drones set to invade the U.S.’s east coast.
Anyway, you can have a look and judge for yourself.
As for me personally, I think that The Epoch Times in ruining its journalistic credibility with their China hit pieces. They have done pretty good reporting in the past with regards to North America. But it seems like they are increasingly becoming an integral part of the CFR-clan, i.e., the Gatekeeper Media or Mockingbird 2.0 controlled by the DOD-CIA-FBI clique.
Addendum #13: 2025-01-17 - China Bad, Very Bad - Bloomberg
I know this is getting repeatedly redundant, but here we go again.
This time with Bloomberg.
And they didn’t make much of an effort to try to make it actually look authentic and believable.
They employed they very same formula as the other false flag pieces I exposed above, namely:
Choosing the same pressitute “journalists” to spew the fairy tales.
Vague language.
Unverifiable sources (parties never return their media inquires by publication time)
Reports they refer to, but never actually provide a link for.
Regurgitating previous “related” articles that are deficient themselves.
Cool hacker group names. In this case it’s “Silk Typhoon and UNC5221.”
etc.
You can have a look at the Bloomberg article (archived here) to see the ridiculousness all for yourself.
The only thing I would add that is noteworthy is that this time, the target of the [supposed] hack is the U.S. Treasury.
This indicatest to me that (like with similar “attacks” I wrote about above"), they are planting the seed that major financial institutions are ripe for a large-scale attack; so that when they do decide to run the full, large-scale, false flag cyberattack it facilitate the task of deciding who to blame, i.e., China.
Addendum #14: 2025-04-19 - WSJ & The Epoch Times continue their propaganda against China
It seems like every week now, we have an article re-iterating old news items (repetition, a form of propaganda) of purported Chinese cyberattacks. And most of them are very poor in that they almost always exclusively use anonymous sources and provide next to no evidence to corroborate their claims.
But this particular article by the Wall Street Journal backed by The Epoch Times (two common outlets for these alleged attacks, as shown in previous addenda above), really showcases their weak reporting (anonymous sources & unprovided evidence). So, let me dissect this one to show you, once more, how this really just amounts to propaganda.
Re-published and cited by countless other “news” outlets, the Wall Street Journal’s April 10, 2025 piece titled In Secret Meeting, China Acknowledged Role in U.S. Infrastructure Hacks really conjures up the fairy tales. To wit, let me obliterate nearly every paragraph of their piece hereunder.
Let me first state that I will be adding emphasis (bolding of text) in order to show you their deceptive tricks.
First paragraph:
WASHINGTON—Chinese officials acknowledged in a secret December meeting that Beijing was behind a widespread series of alarming cyberattacks on U.S. infrastructure, according to people familiar with the matter, underscoring how hostilities between the two superpowers are continuing to escalate.
“Chinese officials” are not identified; this will be a common theme in this article (with one exception). Not identifying officials is a deceptive means to convey their desired information. It is effective because it plants an assumption of validity in the mind of the reader. Moreover, even though it is effective it is also a weak means since by not naming who these officials are, there’s no way to independently verify whether or not such an official made such statements.
Next problem with this initial paragraph is the [false] assertion that the Chinese officials “acknowledged” a wrong doing (in this case being “behind a widespread series of alarming cyberattacks on U.S. infrastructure. This is absolutely ridiculous and laughable for at least two reasons. First, having lived and worked in China for 13 years (having ovserved the behaviours of Chinese officials), I can tell you that such officials would never admit any kind of wrongdoings; it is not in their culture to do so as they would lose face - a critical concept in Chinese culture. Furthermore, would a government of any country admit they were behind a “widespread series” of cyber attacks? Really? Do they think their readers are that ignorant and stupid?
Finally with regards to the opening paragraph, it is stated that a “secret” meeting occurred between officials of China and the U.S. How convenient! Is this cover for a non-meeting? We can’t know since there is no link to an official meeting, as would usually the case for official business of government departments of these two respective countries. Is it possible one was held? Sure. But the lack of any evidence of this stinks.
I have tried to find an indication of the existence of such a meeting by looking at the official Ministry of Foreign Affairs of the People’s Republic of China in their Top Stories (News), Diplomatic Schedule, Spokesperson’s Remarks, and Speeches sections finding nothing on the subject. If any official notice of such a meeting would exist, it would have been stated there.
In addition, I have also verified information posted on the Embassy of the People’s Republic of China in the United States of America (embassy in Washington, D.C.) to see if there was any news or statements made about this secret meeting, and nothing appears on the Embassy Spokesperson's Remarks section of their website to this effect for the period of December of 2024.
Sticking with the first paragraph, the next tactic employed is that of using the infamous “according to people familiar with the matter” . This is very poor reporting, as these so-called people are not identified and thus any assertion made cannot be verified. Moreover, it just adds to it seeming like it is real.
Moving on to the second paragraph:
The Chinese delegation linked years of intrusions into computer networks at U.S. ports, water utilities, airports and other targets, to increasing U.S. policy support for Taiwan, the people, who declined to be named, said.
Again, the problem here is the same as with the first paragraph. The Chinese government would never admit a wrongdoing. Moreover, they state these so-called officials “declined to be named.” How convenient. How ridiculous. In my own personal assessment, these are fabricated lies.
A later paragraph reads:
In the months since the meeting, relations between Washington and Beijing have sunk to new lows, locked in a historic trade war. Top Trump administration officials have said the Pentagon will pursue more offensive cyber strikes against China. Beijing has continued to mine its extraordinary access to U.S. telecommunications networks enabled by a separate breach, attributed to Salt Typhoon, U.S. officials and lawmakers say.
Two things here. The alleged “Salt Typhoon” implies specific targeted Chinese cyberattacks which have frequently been reported on before, but for which I have shown that they have consistently not provided any tangible evidence whatsoever about them (see other addenda above).
Next, we can easily see their anonymous sources, i.e., “U.S. officials and lawmakers.” I mean, how hard would it be to name them if it were really the case? Statements made by U.S. officials and lawmakers almost always appear in some kind of media (social media post, speech, announcement, press conference, hearing, etc.). Yet, the author of this artilce, Dustin Volz, cannot provide it?
The other issue with this paragraph is the “U.S. telecommunications networks” allegation. I have reported on this in previous addenda (above) and though it is of course a possibilty (that the Chinese could hack such infrastructure), there is no tangible evidence to this. Therefore, in my assessment, it appears as yet more predictive programming so as to implant in the minds of Americans that a cyber attack on U.S. infrastructure is becoming more likely.
The following paragraphs reads:
The administration also plans to dismiss hundreds of cybersecurity workers in sweeping job cuts and last week fired the director of the National Security Agency and his deputy, fanning concerns from some intelligence officials and lawmakers that the government would be weakened in defending against the attacks.
Again, the “intelligence officials and lawmakers” are not identified; and thus, we cannot idependently verify these purported statements.
As for the “fanning concerns” part, this just wreaks of some kind of setup. In other words, should the National Security Agency dismiss hundreds of cybersecurity workers (amidst the DOGE job cuts), the danger of increased cyberattacks loom. Sure that can be a logical statement with some validity to it; but, it still stinks of a setup.
Next paragraph:
Officials say Chinese hackers’ targeting of civilian infrastructure in recent years presents among the most troubling security threats facing the Trump administration.
Same problem: unidentified officials meaning we cannot verify this allegation.
In another paragraph:
The Chinese embassy in Washington didn’t respond to specific questions about the meeting, but accused the U.S. of “using cybersecurity to smear and slander China” and spreading disinformation about “so-called hacking threats.”
So, purportedly, the Chinese embassy (a purported employee from the embassy) “accused” the U.S. of “using cybersecurity to smear and slander China” and spreading disinformation about “so-called hacking threats.”
Well, this also stinks since they do not name any specific embassy official who may have made these two statements, nor do they provide any link to such a statement. As I mentioned earlier, I verified the Chinese embassy website for any such information and found nother stated there. If we do a search of these two phrases on Google, all we come up with are news sites that are regurgitating the WSJ’s article’s talking points and nothing comes up from any official Chinese sources (media or government).
Could these statements have been made? Perhaps. And to be fair, these are the type of statements that would be typical of Chinese officials. However, the point here is that there is no source or link to verify that such statements have been made.
The following paragraph reads:
During the half-day meeting in Geneva, Wang Lei, a top cyber official with China’s Ministry of Foreign Affairs, indicated that the infrastructure hacks resulted from the U.S.’s military backing of Taiwan, an island Beijing claims as its own, according to current and former U.S. officials familiar with the conversation.
Same shit, different paragraph: “according to current and former U.S. officials familiar with the conversation.” Really? How convenient.
But at least they got one thing right. Wang Lei is an actual Chinese cyber official. I have found an official web page from the Ministry of Foreign Affairs that shows actual statements of Wang Lei in an interview on the subject of cyber affairs between China and the U.S. Here is an excerpt from that interview [with emphasis added]:
Question 1: US National Security Advisor Jake Sullivan said recently that the US had “sent clear messages to the PRC about what it would actually mean if they acted to disrupt American critical infrastructure and how we would respond”. What is China’s response?
A: We have told the Biden administration explicitly that China rejects US blame on China concerning specific cases without providing any evidence.
So here, Wang does affirm that China rejects blame made on its country by the U.S. since they haven’t provided any evidence.
This WSJ article (and previous ones) indeed do not provide tangible evidence of these alleged attacks.
Continuing with another paragraph from the WSJ article that cites Wang Lei:
Wang or the other Chinese officials didn’t directly state that China was responsible for the hacking, the U.S. officials said. But American officials present and others later briefed on the meeting perceived the comments as confirmation of Beijing’s role and was intended to scare the U.S. from involving itself if a conflict erupts in the Taiwan Strait.
Again, we have statements from unnamed American officials; hence, these cannot be verified. And, these purported U.S. officials “perceived” comments allegedly made by Wang Lei “as confirmation of Beijing’s role and was intended to scare the U.S. from involving itself if a conflict erupts in the Taiwan Strait.”
“Perceived” means that this speculation. Sure, if such statements were made by Wang in this secretive meeting (if it even existed at all), there is the possbility that veiled threats could be made, given the sensitivity of the Taiwan issue. But, this is all merely speculation void of any actual proof that such statements were indeed made by Wang.
Near the end of the article we have:
A Chinese official would likely only acknowledge the intrusions even in a private setting if instructed to do so by the top levels of Xi’s government, said Dakota Cary, a China expert at the cybersecurity firm SentinelOne. The tacit admission is significant, he said, because it may reflect a view in Beijing that the likeliest military conflict with the U.S. would be over Taiwan and that a more direct signal about the stakes of involvement needed to be sent to the Trump administration.
This paragraph cites a China expert on cybersecurity, Dakota Cary from Sentinel One (a cybersecurity firm). Cary also just so happens to be a fellow of the very pro-war, anti-China, Atlantic Council. As such, bias could certainly come into play with regards to Cary’s comments on China.
Here is but one article published on Sentinel by Cary (notice the ominous cover image):
Returning to the paragraph from the WSJ article, we once again have speculation, i.e., “A Chinese official would…” which could indeed make sense as it implies that only at the highest levels (i.e., President Xi Jinping) could approve such an admission (of Chinese hacking U.S. infrastructure); but, this is extremely unlikely given that Chinese leadership has seemingly never made such bold admissions.
Cary goes on to affirm that there was a “tacit admission” by a Chinese official and this is “ignificant.” Sadly though, Cary provides zero proof that such an admission or statement was indeed made. To me at least in my assessment, it seems that Cary made this statement to the Wall Street Journal “journalist” in pursuit of Atlantic Council agendas, and/or to further vilify China; but I will readily admit that this is speculation on my part.
Anyway, so this sums up my analysis of this particular article by the WSJ.
The only other thing I would add is that The Epoch Times, among numerous other outlets, has re-hashed this WSJ article, seemingly to amplify the China boogeyman trope.
Addendum #15: 2025-05-09 - ZeroHedge & Fox News push alleged China buildup in Cuba propaganda
ZeroHedge has been recently re-pushing more anti-China propaganda pieces by the Wall Street Journal and the Epoch Times (as referenced in addenda above). Their editors, known as Tylers, seem to be doing a very poor job at properly vetting the info they are further propagating on their news aggregator site.
The same could be said about the editors at Fox News which are committing the same blatant errors, seemingly pushing anti-China or even pro-war rhetoric against the United States’ main rival.
Here are the articles in question:
ZeroHedge: Satellite Images Uncover China's Buildup In Cuba, Triggering U.S. Spy Concerns, May 07, 2025
Fox News: China's spying in Cuba sparks alarm on Capitol Hill after fresh satellite images show surveillance buildup, May 7, 2025
While these headlines don’t immediately suggest some kind of [alleged] cyberattack on the part of China, I consider it as such given that the ZeroHedge regurgitates a key passage from a letter by the Chair of the House Homeland Security Committee Mark Green (R-TN) and a group of other lawmakers to DHS head Kristi Noem [with emphasis added]:
“The geographic proximity of suspected PRC-linked facilities in Cuba to sensitive U.S. installations, including Naval Station Guantánamo Bay, Kennedy Space Center, Naval Submarine Base Kings Bay, and Cape Canaveral Space Force Station, may enable the PRC to monitor American detection and response capabilities, map electronic profiles of U.S. assets, and prepare the electromagnetic environment for potential future exploitation.”
Firstly note the usual speculative language with the use of the word “suspected” which does not offer a confirmation of the alleged “PRC-linked facilities” in Cuba.
But the key passage here is “prepare the electromagnetic environment for potential future exploitation” which uses vague and somewhat confusing language that seem to suggest that China could be preparing for a kind of EMP assault which, not that dissimilar to a cyberattack, could disrupt or damage infrastructure such as the electrical grid as well as the internet and electronic devices.
Therefore, I will treat this news as in the same category as a cyberattack for this addendum.
So, allow me to show you all the holes in this story – because that’s what it really is, fiction.
Let’s rewind to the beginning of the ZeroHedge article. Here is the first paragraph [with original emphasis left in]:
“China’s aggressive push into Cuba is sounding alarm bells, with fears of covert surveillance operations targeting the United States, a concerning new report from Center for Strategic and International Studies (CSIS) reveals.”
Firstly, ZeroHedge uses the quote above stating it comes from a report (link to the actual CSIS report called At the Doorstep) but this text is nowhere to be found in the report. In addition, the tone used “China’s aggressive push” appears to be subjective, as it is not at all referenced in the report. So, right from the start, this article seems highly propagandistic.
Also, if we look at the report itself and who published it, we can immediately notice bogusness in its assertion. They are trying to make it seem as something serious, but are lacking supporting evidence.
The ZeroHedge article displays the following image from the report:
But upon further inspection, they really seem to be making look as though there is this huge spying facility packed with antenna.
I took the liberty to plug in the coordinates (22° 56' 54.5"N 82° 21' 46.29"W) in Google Maps the report has for this site which they label Bejucal SIGINT Facility for which they took the image, purportedly on April 16, 2025. And if we zoom in a bit in we get the following:
In the (2025) Google Maps screen capture image above, we can see the field which now seems to have 12 long poles which could be antenna. But do these antenna, if that is what they are, seem powerful enough to capture communications from hundreds of miles away in the United States? I am not an expert in this field, but they don’t seem very sophisticated nor powerful.
And there is also a facility labelled ‘Base Espia China’ where the red location mark is which translates to ‘Chinese Spy Base’ in English.
I mean, really? How ridiculous is it that someone (or whomever labelled this place in Google Maps) dubbed this place ‘Chinese Spy Base’ (in Spanish). This really stinks as a ruse.
Furthermore, perhaps to add some kind of authentic feel to it, if we scroll slightly lower (about 800 feef away towards the south) to this purported Chinese Spy Base there’s another one labelled ‘Intelligence Directorate, Republic of Cuba, The 11th’.
Again, this is really ridiculous. Do you really think Cuban intelligence services would call this facility openly as such? What’s even more ridiculous is if you click on this facility, you get the following:
Yep, you can see clearly that this must be some kind of legitimate intelligence agency (sarcasm intended) with a dog gnawing on a bone in the associated image on the left for Google Maps.
There’s another facility nearby labelled ‘Base de Inteligencia China y Rusa’ (English: ‘Chinese and Russian Intelligence Base’). Once more, let’s be serious; do you really think Cuba/Russia/China would stupid enough to label this facility as such? Do they take us for imbeciles?
I’m not sure who gets to label sites in Google Maps, but I suppose (yes, I am speculating here) that it wouldn’t be that hard to do. Was it the Center for Strategic and International Studies (CSIS) who published the report who labelled it? Who knows.
So, why don’t we have a look at exactly who the Center for Strategic and International Studies (CSIS) is, who’s behind them, and what possible motives they may have to push this kind of propaganda.
The Center for Strategic and International Studies (CSIS) is an American think tank based in Washington, D.C. If we look at their about page, we can see the Chairman and CEO of the organisation:
John J. Hamre, the President and CEO is a former U.S. deputy secretary of defense. Thomas J. Pritzker is the Chairman of CSIS and stands out for a few reasons.
Pritzker is an American billionaire heir and businessman who is a member of the Pritzker family, one of the wealthiest families in the United States. He is also the chairman of Hyatt Hotels Corporation. Jay Pritzker, his father, was the co-founder of Hyatt, and his grandparents were Ukrainian Jewish immigrants. Pritzker was named in a deposition filed under oath by Virginia Giuffre related to her being sexually trafficked through the Jeffrey Epstein network; she testified in the deposition that she once was sexually abused by Pritzker (source), though he has denied the allegations. Sounds like a wonderful person to head CSIS.
The Pritzker family has strong ties and is supportive of Israel (see here, here, here, here, here, here, and here).
And, rather notably, Thomas Pritzker also happens to be named as a central figure in Jeffrey Epstein’s criminal sex trafficking operations (see also here); Epstein himself nicknamed Pritzker “Numero Uno.”
Returning to the ZeroHedge article, much of its reporting stems from a letter written by four U.S. Congressmen, namely Mark E. Green, John Moolenaar, Carlos A. Gimenez (who was born and fled from Cuba), and Sheri Biggs.
Remarkably, each of these four members of Congress also have ties to Israel (see their respective support received from the pro-Israel lobby group AIPAC: Carlos Gimenez at $233,687, Mark Green at $228,719, John Moolenaar at $65,000, and Sheri Biggs at $10,500)
That begs the question as to whether Israel may have an interest in helping to promote anti-China sentiment. While I would admit that this is purely speculation, one has to wonder.
What these members of Congress also have in common (with the exception of Biggs) is their apparent hatred or disdain for China and/or the CCP as can be easily seen via their posts and re-tweets on their respective X accounts:
Here’s just one sampling of such anti-China/CCP rhetoric:
And Moolenaar’s X account first nine posts (as seen today on 2025-05-09) show obvious anti-China sentiment.
Something to consider is whether or not these members of Congress have investments in Defense stocks which would undoubtedly profit from war with China.
Regardless, at least three of the four authors of the May 6, 2025 letter to DHS head Noem are staunch anti-China politicians.
The letter itself contains speculative language with the following words: suspected (4 instances), suggest (2), “appear to,” and could.
The second paragraph of the ZeroHedge article also uses the habitual speculative language:
“The worrying findings, drawn from open-source intelligence, expose a suspected circularly disposed antenna array (CDAA) at Cuba’s Bejucal signals intelligence site, just a stone’s throw from Havana, according to Fox News. The antenna could zero in on radio signals from 3,000 to 8,000 miles away—putting U.S. military bases and even Washington, D.C. within range, the news outlet noted.”
In the absence of specific confirmation or evidence of the type of antenna used, stating that it “could” intercept communications from “3,000 to 8,000 miles away” is quite laughable, given the 2025 Google Maps image I posted above.
The article also references another Congressman, Rick Crawford (also a recipient of the AIPAC lobby) with fierce rhetoric on China:
“The CCP’s poisonous alliance with Cuba has posed significant threats to U.S. national security for decades.”
In his May 8, 2025 post on X from which the article draws from, he continues:
“Their alleged involvement in signals intelligence hubs in Cuba is outward, unconcealed adversarial behavior against the U.S. The CCP’s actions are becoming increasingly more bold and thereby detrimental to Western Hemisphere security.”
As you can see, Crawford fares no better in his assertion by using the “alleged” language in his post.
Furthermore, the ZeroHedge article references a 2023 Wall Street Journal article, Cuba to Host Secret Chinese Spy Base Focusing on U.S., which only uses anonymous [intelligence] sources as well as the usual speculative and ill-evidenced language with the same modus operandi for the two articles the WSJ story links to.
I swear, they really really have the rinse-and-repeat propaganda tactic thing down to an art form.
Moving along to the Fox News article, China's spying in Cuba sparks alarm on Capitol Hill after fresh satellite images show surveillance buildup, it just repeats more of the same quotes, talking points and signature propaganda tactics. For example, their speculative language includes: “appears to be,” and “highly likely.”
To give Fox News some credit, though, they do at least state that “China has denied having any ties to surveillance infrastructure in Cuba, and nothing in the unclassified space shows indisputable links to China.”
To conclude this addendum, I guess that in addition to the usual anti-China outlets Wall Street Journal, the Epoch Times, AP, POLITICO, Reuters, and Bloomberg, we will also need to keep an eye on ZeroHedge and Fox News going forward to see if their editors decide to poorly vet such kinds of articles they post on their platforms.
[Addition on 2025-05-25]: Here’s yet another spin on this bogus “story” but from The Epoch Times (surprise surprise). But at least, they do label it Opinion so we can give them credit for that.
The Epoch Times - Cuba Now a Strategic Battleground for China Against the US, May 24, 2025
I won’t even bother to go over the ridiculousness of it all, as I think you all know their deceptive ways by now.
Addendum #16: 2025-05-16 – Reuters “Rogue communication devices found in Chinese solar power inverters” propaganda
Back to Reuters again folks.
And this “article” (I put that between air quotes because it is more of a propaganda piece than anything else) shatters the record for the number of anonymous sources cited (see below).
Here are the links to the article in question and those who blindly regurgitated it:
Reuters – Rogue communication devices found in Chinese solar power inverters, by Sarah Mcfarlane, May 07, 2025
ZeroHedge – "Rogue" Devices Found Hidden In Chinese Solar Panels Could "Destroy The Grid", May 15, 2025
Modernity News – Modernity News: “Rogue” Devices Found Hidden In Chinese Solar Panels Could “Destroy The Grid”, by Steve Watson, 14th May 2025
Okay, so let me focus on the Reuters “article” by beginning with the insane amount of anonymous sources used by its author.
Here is a summary of each occurrence, along with the number of times they are stated/referenced:
“two people [said]” – 5 times
“one of them said” – 1 time
“three people with knowledge of the matter said” – 1 time
“experts [said]” – 4 times
“two former government officials said” – 1 time
“The DOE spokesperson said” – 1 time
“said a NATO official” – 2 times
“a Sol-Ark spokesperson said” – 1 time
“A spokesperson for the Chinese embassy in Washington said” – 1 time
more: “spokesperson said” – 2 times
Congratulations Reuters, as this totals the a STAGGERING 19 UNSPECIFIED SOURCES / OCCURRENCES which must be close to a record or your personal best!
So, let me dissect some other absurdities from this propaganda piece.
Firstly, let us look at its title: “Rogue communication devices found in Chinese solar power inverters.”
The word “rogue” seems to imply some malicious or criminal intent on the part of China for these so-called “Chinese solar power inverters.” It conveys a guilty as charged or guilt by association tone.
Also, as we will see shorty, this is quite misleading or deceptive since zero proof is given as to whether these devices are actually doing what is alleged.
Furthermore, as individuals are super busy in today’s information overload society, they may only just read the title of the article without reading its contents, giving them an immediate and lasting impression of culpability on the Chinese.
The piece provides a Summary which includes four points before its first paragraph:
Rogue communication devices found in Chinese solar inverters
Undocumented cellular radios also found in Chinese batteries
U.S. says continually assesses risk with emerging technology
U.S. working to integrate 'trusted equipment' into the grid
This is effective, as the first point has the word “rogue,” and the second has the phrase “undocumented.” The latter is quite vague; it says “Undocumented cellular radios” implying that these alleged “cellular radios” are indeed present in the solar panel equipment.
But, they provide zero proof of this which thus confirms that it is nothing more than speculation, as no evidence or citations from sources are provided to corroborate it.
As I pointed our earlier, they do cite experts, by they are unidentified. Therefore, it is impossible for the reader, journalists, or news organisations to independently verify the claims.
Also, most of the sources are anonymous and cannot be verified or confirmed.
So, when the author makes a statement such as “Both declined to be named...” it just makes the article riddled with a lack of credibility and gives its author carte blanche to make up any tale that conveniently fits the narrative. This is propaganda or subjective speculation at best, not proper reporting.
As with most other propaganda pieces analysed in my addenda from above, speculative language is certainly not lacking. As an example, consider the following paragraph [with emphasis added]:
“We know that China believes there is value in placing at least some elements of our core infrastructure at risk of destruction or disruption," said Mike Rogers, a former director of the U.S. National Security Agency. "I think that the Chinese are, in part, hoping that the widespread use of inverters limits the options that the West has to deal with the security issue.”
At least for this one they used an actual identified source; but that source only offers his subjective thoughts as is revealed by his choice words: believes and think.
“The two people declined to name the Chinese manufacturers of the inverters and batteries with extra communication devices, nor say how many they have found in total,” the Reuters article states.
So, the article is based on supposed claims that Chinese devices contain these so-called “extra communication devices,” and yet there is no mention whatsoever of the specific Chinese company(ies) or supplier(s) of said devices, nor are any of those devices identified. How convenient. This is tantamount to hearsay, as there is no forthcoming information identifying the alleged Chinese companies so that we can actually research and verify the claims or allegations made, nor make inquiries to the companies to obtain their official comments on the matter. Heck we don’t even know if such kind of [relaying] devices actually exist, since not a single example of such kind of device is referred to in the article.
A U.S. official that is cited in the article is August Pfluger, a Republican Congressman from Texas who is arguably a China hawk as well as, like other Congressmen mentioned in the previous addendum above, a recipient of funds from the AIPAC lobby:
“The threat we face from the Chinese Communist Party (CCP) is real and growing. Whether it's telecom hacks or remotely accessing solar and battery inverters, the CCP stops at nothing to target our sensitive infrastructure and components.”
Regarding Pfluger’s assertion from above about “telecom hacks,” he is undoubtedly referring to the incidents described in previous addenda above – which I have largely debunked. Overall, his statement is rather vague and unsubstantiated.
Furthermore, his brother Karl is the president of an oil and energy company in Midland, Texas; so, there could be some inherent conflicts of interest at play here.
“It is about time we ramp up our efforts to show China that compromising us will no longer be acceptable,” Pfluger told Reuters.
What exactly does he mean by “to show China”? Does that sound diplomatic and objective to you? To me at least, it conveys an antagonising or hawkish tone.
Finally, it must be re-stated that the author of the Reuters piece fails to mention the names of the spokespersons for the DOE (United Sates Department of Energy) and NATO which strays from prevailing journalistic norms. Usually, official spokespersons for government are identified by name unless it can put them in some kind of danger or that the matter is of a very sensitive consideration.
So there you have it folks. I’ve made three media requests to the outlets which have pushed this story so as to attempt to obtain clarification from them on the matter.
Media Requests I’ve made
I have sent a media request to Sarah Mcfarlane from Reuters asking her to reveal the identities of the spokespersons for the DOE and NATO as well as the “experts” she cited in her article. I have yet to receive a response, but will update this addendum should it be forthcoming.
I have also sent media requests via email to both ZeroHedge and Modernity News asking them whether they have received any remuneration for posting their article (linked above). I have yet to receive a reply, but will update this addendum should they reply.
It is no secret that on social media accounts such as X, those with over about 50k followers do receive financial offers and remuneration for posting (pushing) certain posts; this was confirmed to me by a fellow investigative journalist of mine whom has received (but not accepted) such offers.
[END OF ADDENDA section]
This article is also published in:
And I was interviewed (alternate link here) by investigative journalist Johnny Vedmore in which we talked about this and other happenings. You can watch a video excerpt below:
Please share far and wide.
God bless.
In Peace & Liberty,
Most articles are free, but please support the work of this independent journalist by considering a paid subscription to his Substack (for only $5 a month, or $50 a year) and following his Twitter. You can also buy him a coffee.
Disclaimer:
None of the information or advice presented in this post is to be taken as financial, investment, or medical advice. See the author’s About page for full disclaimer.





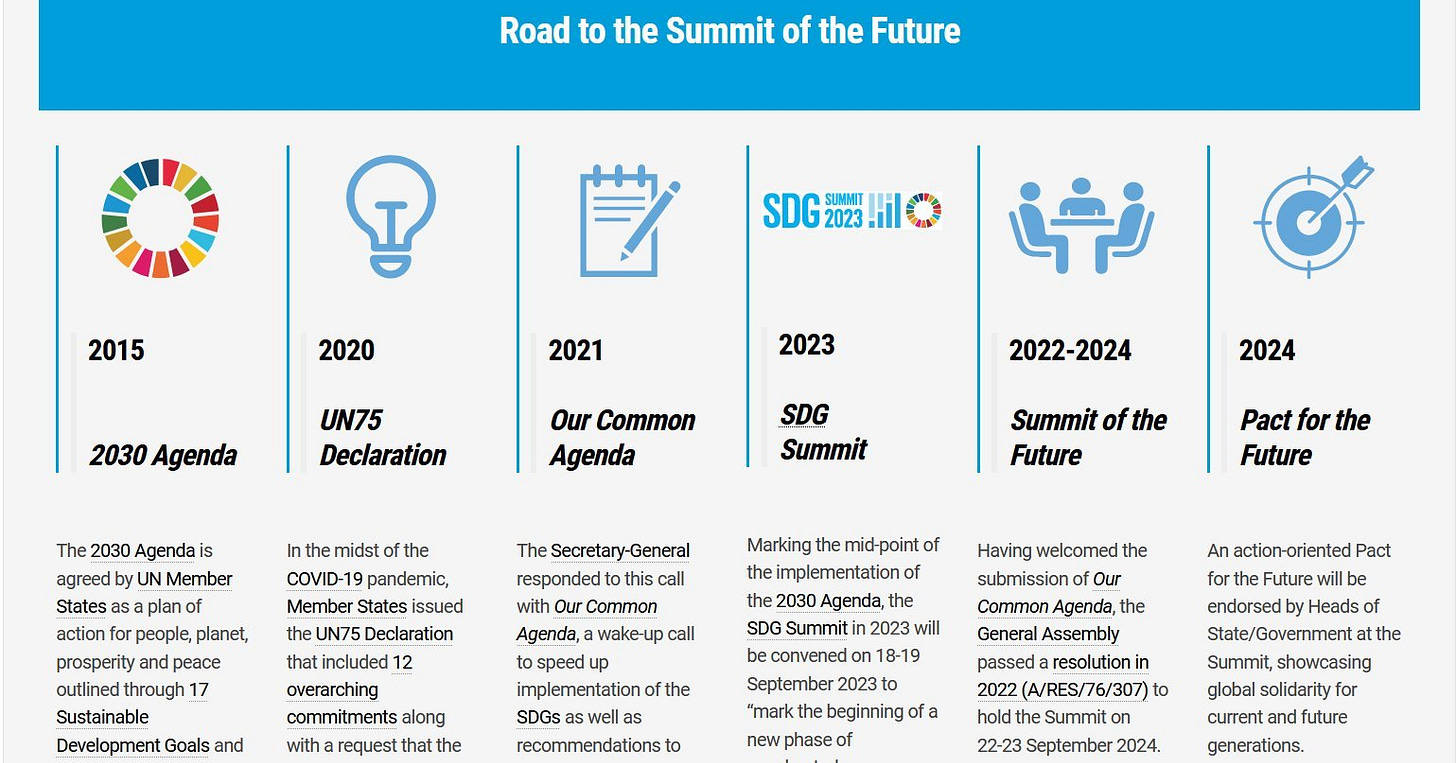








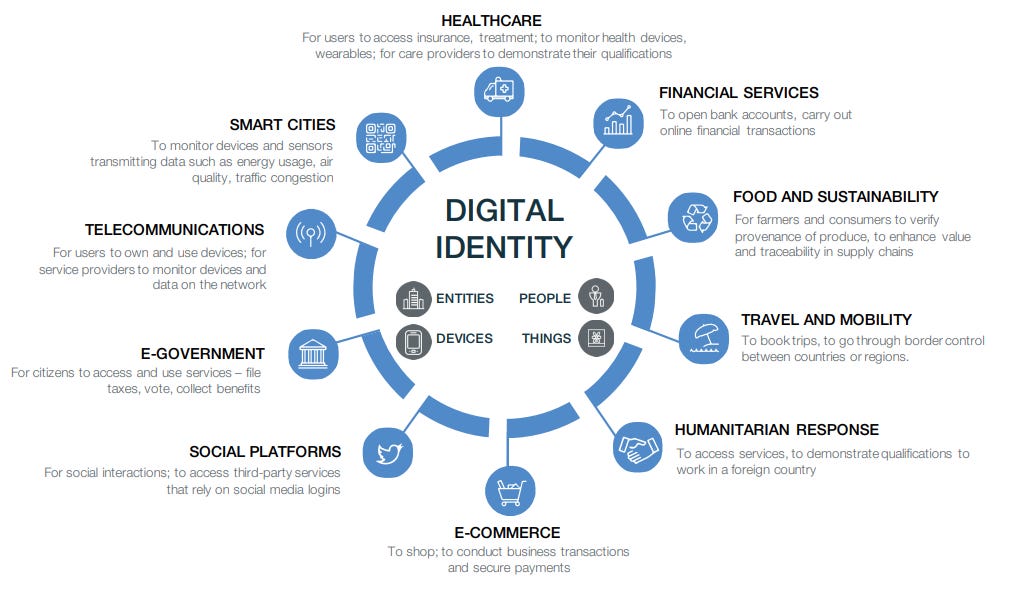

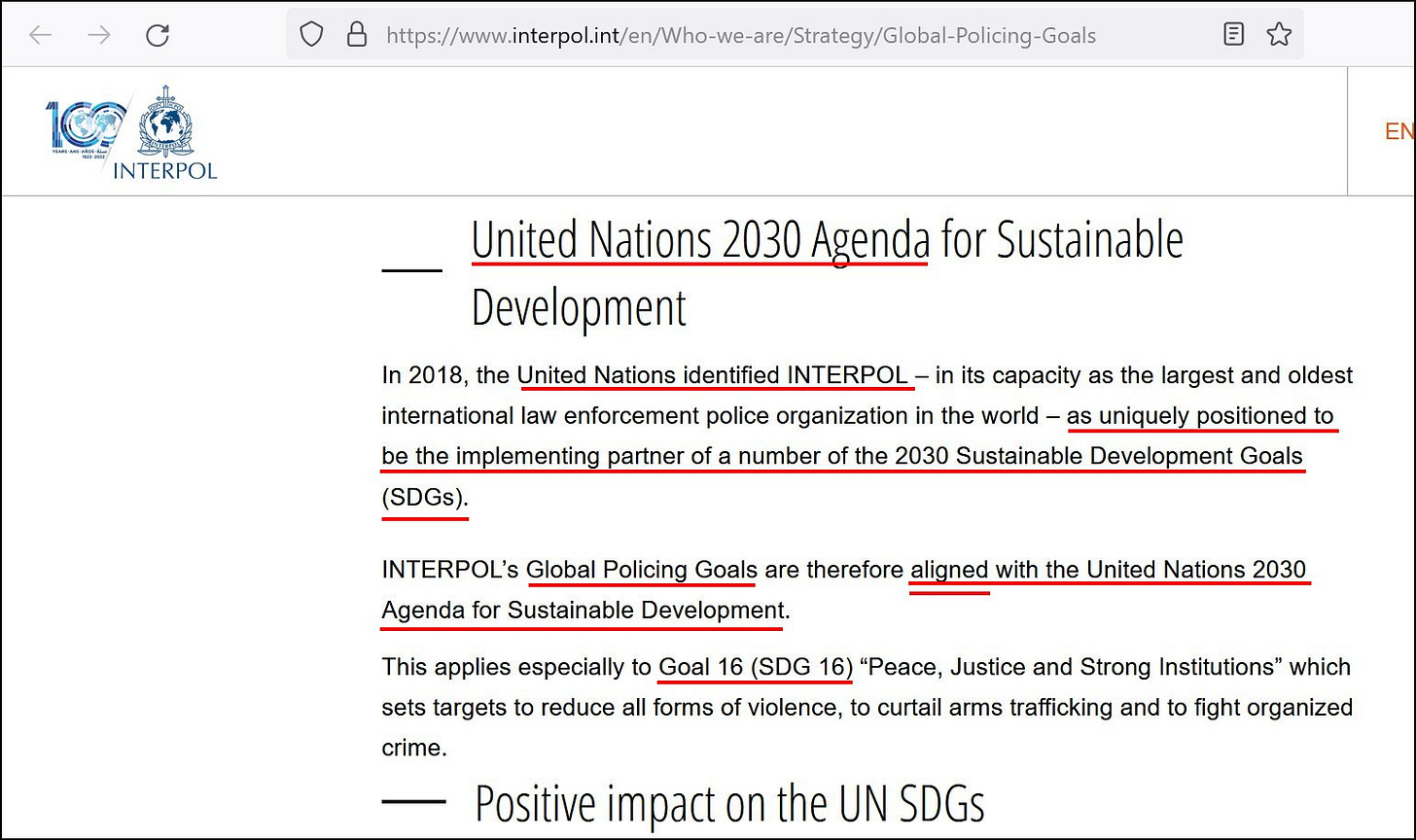
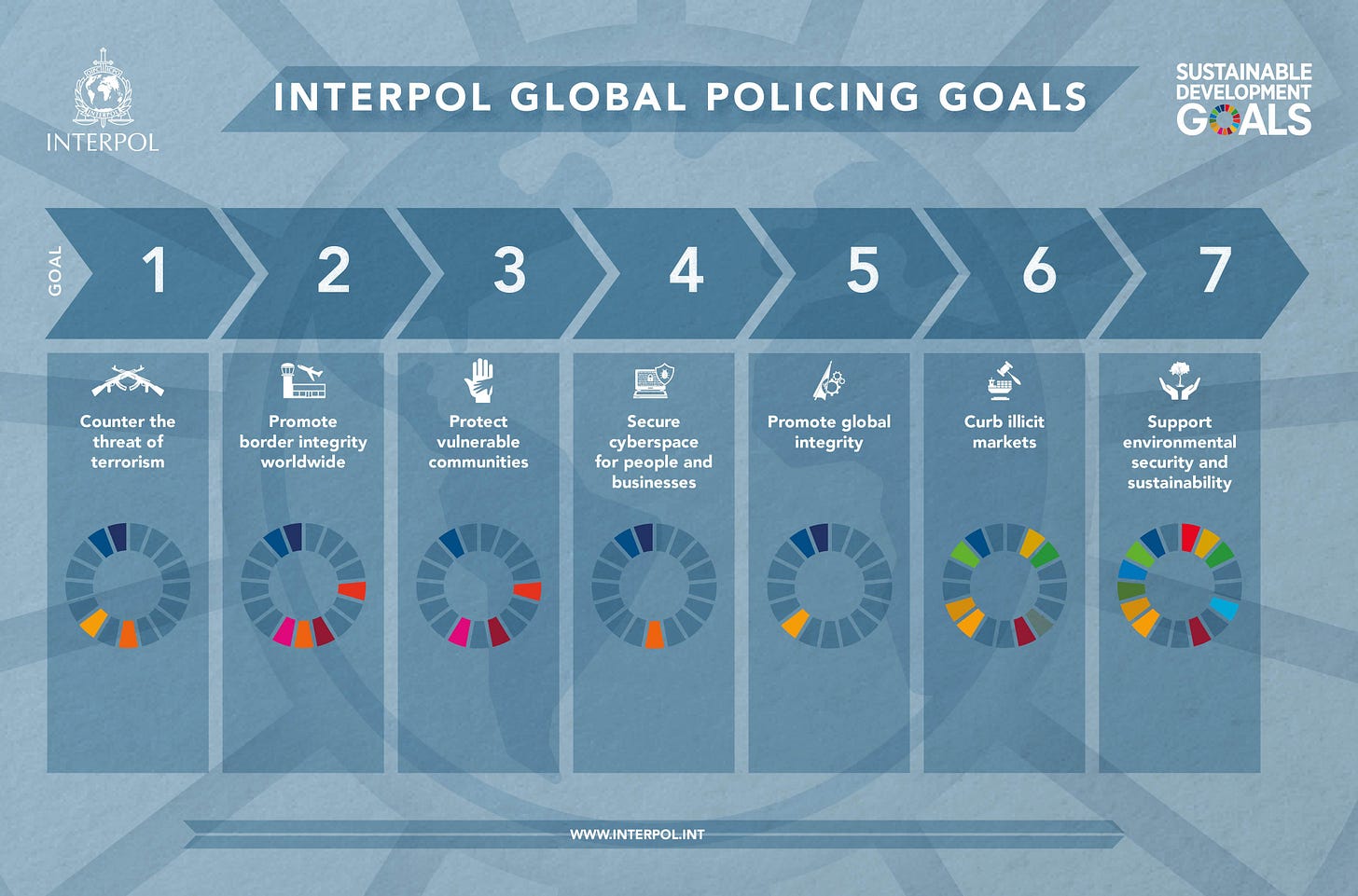
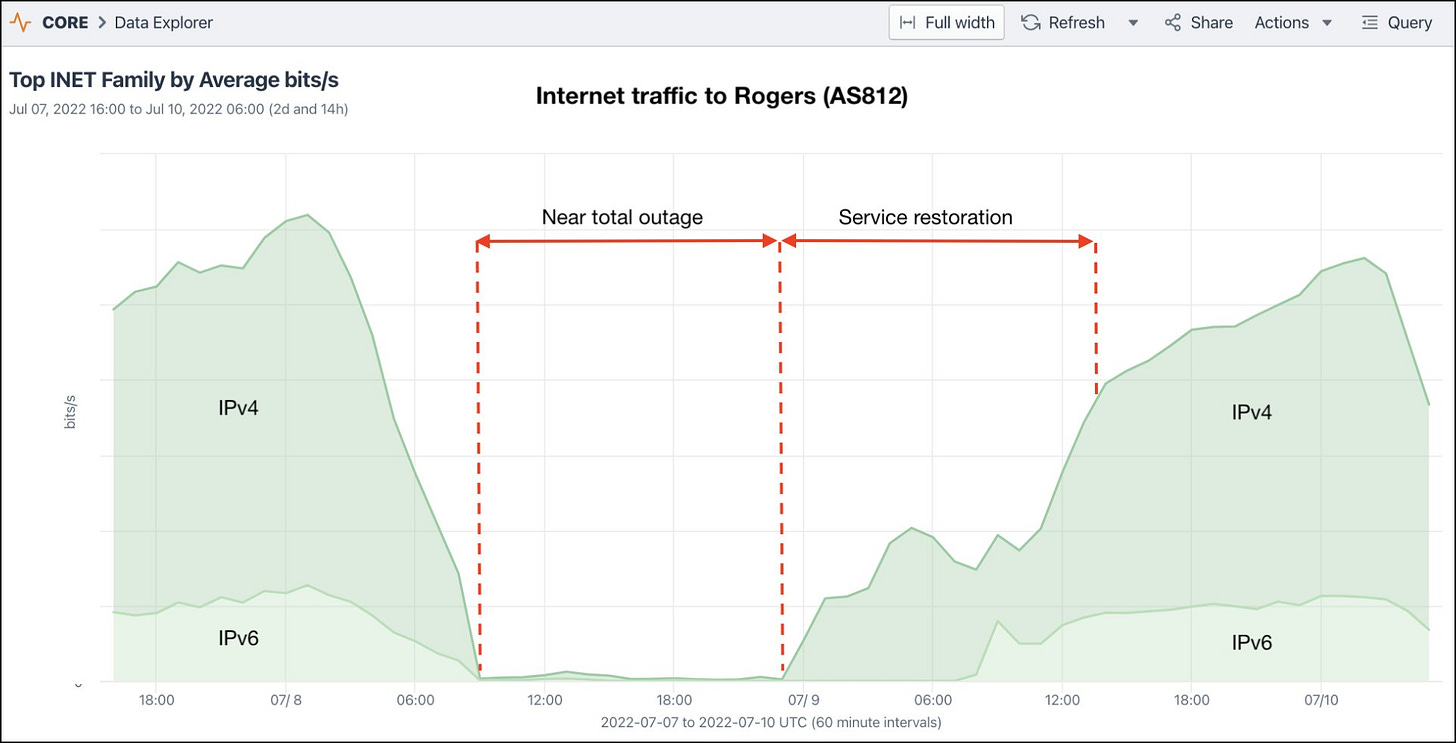









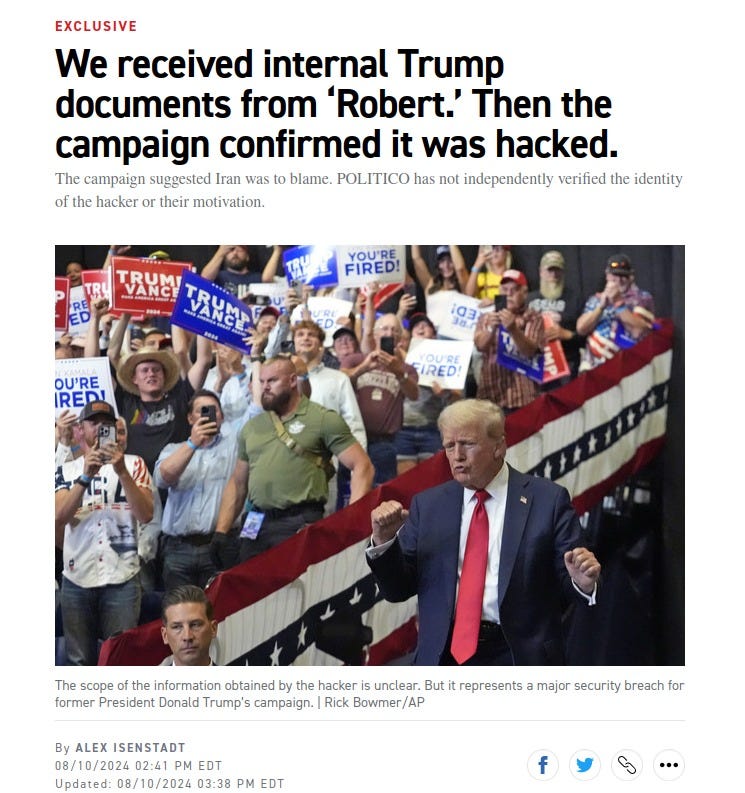









The UN "Universal Declaration of Human Rights" (UDHR), adopted in 1948 and promoted by Eleanor Roosevelt, is another set of noble sounding platitudes similar to the "Sustainable Development Goals". After enumerating these "rights", note this legalistic caveat near the end:
29.3: "These rights and freedoms may in no case be exercised contrary to the purposes and principles of the United Nations." un.org/en/about-us/universal-declaration-of-human-rights
Who defines the "purposes and principles" of the UN organization, which supercede these so-called "universal rights"? So much for the vaunted "freedom of thought", "freedom of expression", "freedom of movement", "right to work", etc. for anyone who fails to conform to their agenda, as recently demonstrated.
Eleanor Roosevelt also promoted the Luciferian "Great Invocation" produced by Alice Bailey and the Lucis Trust, a UN affiliated NGO. See article: lucistrust.org/the_great_invocation/eleanor_roosevelt_reads_the_great_invocation
See also the Lucis Trust "World Goodwill" project:
lucistrust.org/world_goodwill/supporting_the_work_of_the_united_nations
March 11, 2024 is also a likely date for the event.