National Cybersecurity Exercise Conveniently Scheduled for Nov. 5, Election Day (and Guy Fawkes Day)
Commentary by Dan Fournier, published Wednesday, Oct. 23, 2024, 15:20 EDT on fournier.substack.com
A demonstrator wears a Guy Fawkes mask during an “Occupy Congress” rally at the West Front Lawn of the Capitol on January 17, 2012. Photo source and credit: Alex Wong, Getty Images.
Reminiscent of how a simulated exercise of a terrorist attack was scheduled and conducted on September 11, 2001, there is now an equally suspicious event planned for November 5, 2024, Election Day in the United States.
Arguably the most important and pivotal election in U.S. history, strangely coinciding with Guy Fawkes Day, a three day Homeland Security Conference 2024 event will begin on November 5 with a focus on cybersecurity and critical infrastructure.
The event will be held by the Atlanta Chapter of the AFCEA, an international nonprofit 501(c)6 organization whose members and constituents include professionals in military, government, industry and academia.
Its mission seeks to increase “knowledge through the exploration of issues relevant to its members in information technology, communications, and electronics for the defense, homeland security and intelligence communities.”
AFCEA’s International Board of Directors is comprised of several former U.S. Military personnel as well as military contractors, intelligence, and tech companies from the private sector.
The third paragraph of the above screenshot for the event reads as follows [with emphasis added]:
“The U.S. Department of Homeland Security (DHS) works to strengthen critical infrastructure security and resilience by generating greater understanding and action across a partnership landscape. This is achieved by working with private and public infrastructure stakeholders to resolve infrastructure security and resilience knowledge gaps, inform infrastructure risk management decisions, identify resilience-building opportunities and strategies, and improve information sharing among stakeholders through a collaborative partnership approach. The Cybersecurity and Infrastructure Security Agency (CISA) leads the effort to enhance the resilience of the nation's physical and cyber infrastructure by bringing resources to your fingertips. Only working together can we defend against today’s threats and collaborate to build secure and resilient infrastructure for the future.”
Notably, the AFCEA works with the U.S. Department of Homeland Security (DHS) and the Cybersecurity and Infrastructure Security Agency (CISA).
Firstly, it is important to observe that the head of the DHS is Alejandro Mayorkas who is primarily responsible for the influx of migrants into the U.S. via the southern border and whose Secret Service (which his department oversees) grossly failed (or helped to enable) security surrounding the Trump Assassination Attempt of July 13.
CISA, the operational lead for federal cybersecurity and the national coordinator for critical infrastructure security and resilience is directly concerned with election interference matters, recently launching the #Protect2024 initiative whose mission is to:
“Help election officials and election infrastructure stakeholders protect against the cyber, physical, and operational security risks to election infrastructure during the 2024 election cycle.”
The #Protect2024 page also emphasises increased cybersecurity risks during the election:
“For years, America’s adversaries have targeted U.S. elections as part of their efforts to undermine U.S. global standing, sow discord inside the United States, and influence U.S. voters and decision making. We expect 2024 to be no different. U.S. elections remain an attractive target for both nation-states and cyber criminals. As we move into the 2024 election cycle, CISA and our partners in the federal government are positioned to support election officials and private sector election infrastructure partners in addressing the physical, cyber, and operational security risks they face.”
The above video message was communicated by CISA’s Director Jen Easterly.
In August of 2021, Homeland Security Secretary Alejandro Mayorkas participated in the swearing in of CISA Director Jen Easterly in Arlington, Virginia who was appointed to the position thenceforth focusing on beefing up the agency’s disinformation and misinformation team and establishing a ‘rumor control’ site to counter “false claims in future elections.”
Secretary of Homeland Security Alejandro Mayorkas at CISA's current headquarters in Arlington, Virginia on August 9, 2021. Photo source: Wikipedia.
Since mid-2023, CISA identified Iran as an advance cyber threat, citing intelligence from the Office of the Director of National Intelligence (DNI) who is headed by Avril Haines, a former deputy director of the CIA under Obama and Biden.
Citation taken from CISA’s Iran Cyber Threat Overview and Advisories web page.
Like Mayorkas, U.S. Attorney General Merrick Garland and Anne Neuberger, Deputy National Security Advisor for Cyber and Emerging Technology, Avril Haines is Jewish according to the Jewish Telegraph Agency; this indicates, take it as you will, another form of potential foreign influence due to their strong ties with Israel, especially given the Zionist nation’s current hold on the U.S. Congress and U.S. Military.
Notice the language used in the advisory from the DNI that CISA cited above; it says “Iran may attempt...”
I’ve reported extensively on these kinds of deceptive and ill-founded allegations in several addenda from my August 31, 2023 article titled Cyber Attack Crisis which predicted a large-scale cyber attack on U.S. infrastructure that would be blamed on either Russia, China, or Iran.
Incidentally, my last two addenda in that article focused on laughable allegations against Iran, Israel’s primary foe in the Middle East. Therein, I dismantled these allegations by exposing the baselessness of their purported threats, including so-called hacks on Trump’s Presidential Campaign.
It would appear, once more, that ill-founded potential cyberattack allegations by Iran are conveniently (and rather timely) re-surfacing amidst the impending U.S. Election contest.
More on the AFCEA Atlanta large-scale tabletop cybersecurity exercise
Digging further into the the AFCEA Atlanta large-scale tabletop cybersecurity exercise we can notice that on November 5 between 12:30 pm to 5:30 pm – a prime period when voters will be casting their ballots across the nation – an All Hands on Deck meeting will take place whereby participants from federal, state and local agencies will be focusing on critical infrastructure.
On November 6, Brig. Gen. Paul Fredenburgh III (Ret.) and Sebastian Barron, the Metro Atlanta Representative for the Office of Georgia Governor Brian Kemp will be speaking. It should be recalled that in January 2021, after the election of President Joe Biden, Kemp was criticized by outgoing President Donald Trump with claims of voter fraud and for certifying the results.
Also on November 6, Tanya Simms, Chief of the [new] Office of the National Manager of the National Security Agency (NSA) and former Director for Cyber Policy and Programs for the Office of the National Cyber Director will be speaking.
The “Office of the National Manager (ONM) for National Security Systems (NSS) exercises presidential authority by issuing guidance and mitigations for critical cyber threats and vulnerabilities,” reads the session description for this talk (with hyperlinks added).
Notice the “exercises presidential authority” phrase which suggests a greater role by the NSA in the event of a cyber incident.
Moreover, the aforementioned Anne Neuberger, an Orthodox Jew from Brooklyn, just happened to be named Deputy National Manager (DNM) for the NSA and Director of its Cybersecurity Directorate in 2019.
A Platinum sponsor for the AFCEA is the Homeland Defense & Security Information Analysis Center (HDIAC), a component of the U.S. Department of Defense’s (DOD’s) Information Analysis Center (IAC) which is an enterprise that advises on a range of areas including Critical Infrastructure Protection and has recently (Sept. 2024) secured a $33 billion contract with the DOD.
DHS’s Office of Intelligence & Analysis (I&A)
With regards to mitigating cyber threats (as noted in the cited statement above), it should also be observed that the DHS’s Office of Intelligence & Analysis (I&A) is the only Intelligence Community (IC) element statutorily charged with delivering intelligence to state, local, and tribal levels and private sector partners.
In other words, in the event of a cyber attack on U.S. Election critical infrastructure, the I&A would be the entity advising DHS - and inherently the White House - on the threat along with mitigation measures to be employed.
The Office of Intelligence & Analysis (I&A), established in the wake of the September 11, 2001 attacks, is headed by its Under Secretary for Intelligence and Analysis Kenneth L. Wainstein.
Special Measures during a National Security Incident
An election-related cybersecurity incident – whether authentic or staged – could effectively put the United States under a state of declared National Emergency.
Should such an incident occur, it is very well possible that nationwide tensions could ensue, putting the country into a state of uncertainty or even chaos.
Of particular note was a very recent (September 27, 2024) Directive 5240.01 issued by Department of Defense which authorises the military to assist local law enforcement to use lethal force on Americans during domestic disturbances.
Moreover, such a cyber event could be used as a justification to delay the confirmation of the winner of the 2024 Presidential Election on the grounds that foreign interference may have compromised the election’s integrity.
In such an occurrence, it could be several weeks or months until clarity regarding the winner becomes determined.
What are your thoughts regarding this particular tabletop National Cybersecurity Exercise?
Leave them in the Comments section below.
Addendum 2024-10-26 - The Conference is now postponed!
As per an announcement on their conference page (archived on Oct. 25 here), the AFCEA Atlanta event is now postponed!
The reason cited is (circled in red above) due to:
A rapid and unanticipated rise in rhetoric and threats stemming from disinformation about the purpose of the event and its proximity to Election Day contributed to the decision to postpone.
They announcement doesn’t clarify what they mean by “disinformation” which is one of the reasons for postponing the event.
So, it looks like they have received a fair amount of public scrutiny - like for this post which has already climbed to the 5th most viewed post on my Substack (with nearly 4,300 views) and decided that they couldn’t risk going through with it.
Power to the people!
Addendum 2024-10-26 - Ransomware Attack Simulation scheduled for Nov. 5 by Cybereason
Just when we thought things got quieter (see previous addendum above), it has now come to my attention that there is a Ransomware Attack Simulation scheduled for November 5, 2024 at 10:00 EST by a cybersecurity firm called Cybereason.
The “Attack Simulation” is one which simulates a ransomware attack, as per the description of the event (archived here).
Cybereason is described as an American cybersecurity technology company which was founded in 2012. It has offices around the world, including one in Tel Aviv (Israel) and another in London (UK).
Cybereason major investors include Softbank Group and Lockheed Martin Corporation, one of the largest military contractors to the United States Government.
Though this simulation doesn’t specifically state that it is concerned with election systems interference, what remains particularly noteworthy is who founded Cybereason.
Cybereason’s Israeli Military/Intelligence Link
The co-founder and former CEO of Cybereason is Lior Div (Lior Div Cohen) an expert in hacking operations who was previously a member of the Israeli Defense Forces (IDF) and most notably part of its Unit 8200 cyber security unit.
Just last month, I interviewed Terry Wolfe on my podcast and we talked about Unit 8200 of the IDF (click link for more on the unit and for our talk).
Though Lior Div is no longer the CEO of Cybereason since January 11, 2021 it should be observed that he along with two former members of Unit 8200 - namely Yossi Naar and Yonatan Amit - built the enterprise.
As per a Dec. 01, 2016 article, Div spent six years with the Unit “running in the shadows” when suddenly the efforts of the Israeli and American governments to launch sophisticated attacks on the computer systems running Iran’s main nuclear enrichment facilities were thrown into the spotlight.
Div also said that this experience was the first example to the world that people were using software as a weapon to achieve military goals.
The article further states [with emphasis added]:
Another formidable aspect of Cybereason is its in-house intelligence unit. Div and his co-founders have built an intelligence group that collects and analyzes information like the military would, with many of the unit’s members coming from organizations like the NSA and Unit 8200.
So, we do have confirmation that members come from both the IDF’s Unit 8200 as well as from the National Security Agency (NSA).
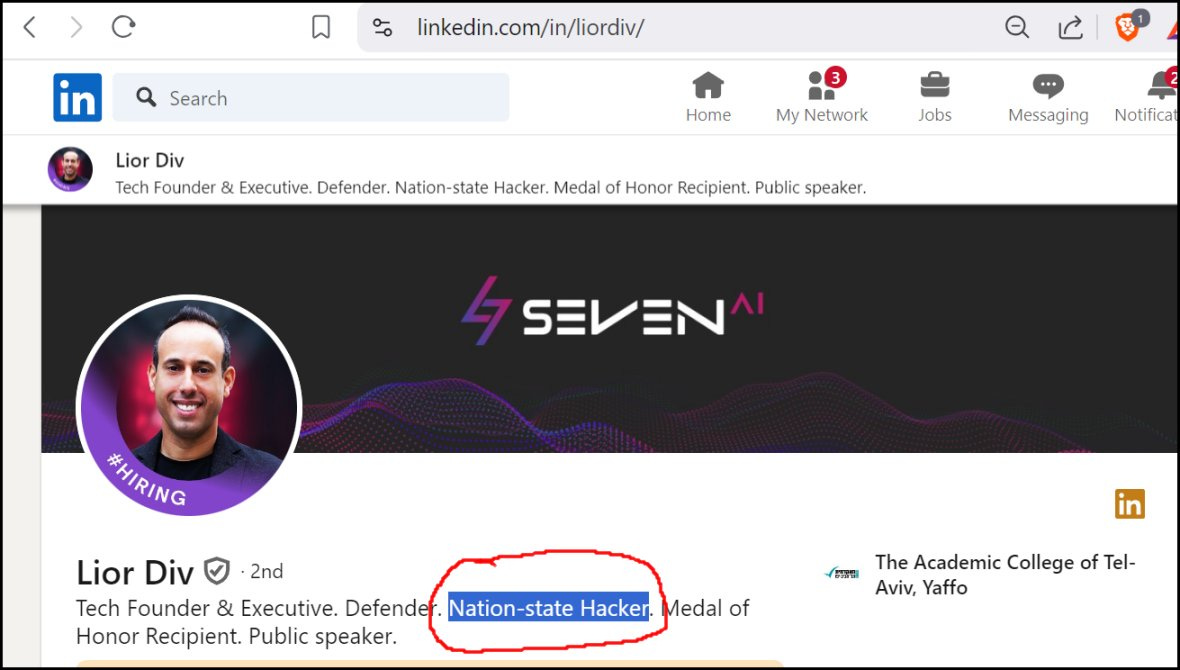
Screenshot of Lior Div’s LinkedIn page showing his “Nation-state Hacker” self-description (circled in red), captured on 2024-10-26.
In a more recent, June 29, 2020, interview published by Yahoo Finance, Cybereason co-founder Lior Div stated that during his time in the Israeli Defense Forces, he was trained to handle offensive cyber operations with a mindset that “has more to do with offense than defense.”
When describing the strengths of his cybersecurity company, he said that a big differentiator is their ability to protect organizations from nation-states and other hacking groups.
When asked: What are the reasons hackers decide to attack a company? by the interviewer, he provided the following, rather strange, reply [with emphasis added]:
There are many reasons: for financial or political gain, to sow doubt, to create diversions as part of another campaign. Recently, we’ve been seeing an uptick in hacking activity as it pertains to IP, specifically around the coronavirus, which is more likely than not an attack meant for political gain. The current state of affairs has created a struggle for a new global order, and cyber will certainly play a role in a nation’s attempts to get ahead.
“The current state of affairs has created a struggle for a new global order” and “cyber will certainly play a role in a nation’s attempt to get ahead,” is a rather odd response to this particular question, wouldn’t you say?
I am still not sure what to make of this statement.
Apart from the date on which this upcoming ransomware attack simulation will take place, November 5, it is difficult what to make of this scheduled exercise.
Cybereason hasn’t posted much on its X page since mid-2023 - which in itself would appear quite odd given its [supposed] 16.3K followers and considering that they are a large outfit with over a thousand employees (heavily based in Israel) with a valuation of over $3 billion, despite very little information posted on their website regarding who their clients are.
I suppose we will have to wait and see what occurs on November 5, but something certainly doesn’t smell right about this one.
Support Independent Journalism
As an independent journalist, I take great care and pride in providing my audience with quality investigatory work and writings.
This is the kind of work that is seldom reported on in as much detail by the mainstream media, for they also tend to avoid the subjects and sometimes controversial topics that I, myself cover.
As an independent, I get paid very little for this work, for the bulk of my revenue comes from Substack subscriptions, and I am mostly surviving and supporting my family by means of personal savings.
You can support my work by considering a paid subscription to my Substack – Dan Fournier’s Inconvenient Truths (for only $5 a month, or $50 a year).
For one-time donations, you can also buy me a coffee.
If you are unable to support my work financially, it is greatly appreciated if you can share it on your social media feeds, for this brings additional exposure (and much needed eyeballs) which can lead to new paid subscribers.
Your comments are most welcome and appreciated and can be given in the Comments section below.
I sincerely thank you for your time and support.
Disclaimer:
See the author’s About page for full disclaimer.
Follow me on X, formerly known as Twitter:
I can also be followed on Primal (which is a Nostr decentralised alternative to X that cannot be censored, and where users cannot be de-platformed). If you are tired of X, you can create your own account on Primal.











I'm so sick and tired of all these doomsday prognosticators. If we listened to any/all of them, the world would've long been over with by now. By hyping all this crap, it's enabling self-fulfilling prophecies just so someone out there can say, "See, I told you so!" As a devout Christian I'm secure in my salvation and God's sovereignty. The election will come and go, and whoever wins is by God's design. There will most certainly be controversy one way or the other, but the world will not come to an end. But even if it did, I'm saved and in a better place! Hallelujah!!!
Another excellent, in-depth piece, Dan. This piece jibes with my recent essay where I try to show how important the Censorship Industrial Complex is to efforts to get society-destroying programs implemented. Of course, this is done under the guise of fighting "disinformation."
As your article further confirms, the Powers that Be are fixated on fighting disinformation - which is really concealing important truths from citizens.
IMO, the expansion of the Censorship Industrial Complex proves evidence "the fix is probably in" on the coming election. The Deep State members would have abandoned this program if the fix wasn't in.
https://billricejr.substack.com/p/logic-tells-me-the-fix-is-in